
The No More Ransom project celebrates its sixth anniversary today after helping millions of ransomware victims recover their files for free.
Launched in July 2016, No More Ransom is an online portal and a public-private partnership created by law enforcement (Europol and the Dutch National Police) and IT security companies (Kaspersky and McAffee).
Today, the No More Ransom project includes 188 partners worldwide, including BleepingComputer, who joined the project in 2018.
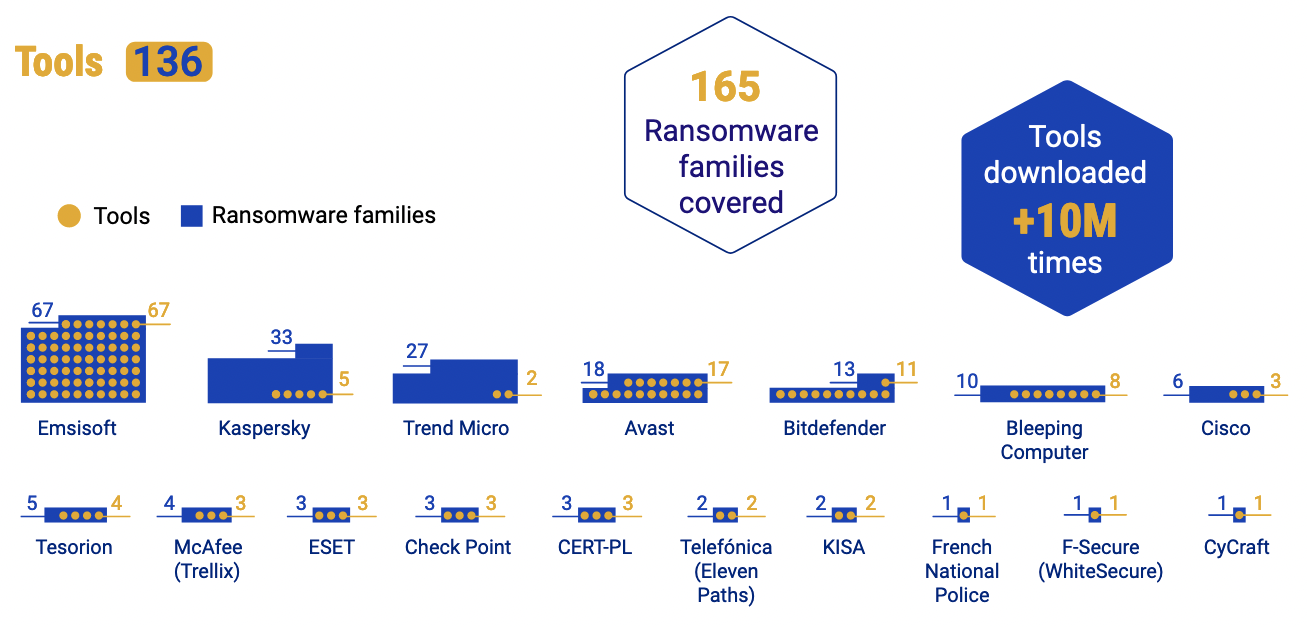
While initially, it provided only four ransomware decryptors, it has now grown to host over 100 free decryption tools for dozens of ransomware families.
"Six years later, No More Ransom offers 136 free tools for 165 ransomware variants, including Gandcrab, REvil/Sodinokibi, Maze/Egregor/Sekhmet and more," Europol said Tuesday.
During the six years since its launch, the initiative has provided more than 10 million people with free decryptors to recover their files without paying cybercriminals.
As Europol revealed last year, when No More Ransom celebrated its fifth anniversary, "this prevented criminals from earning almost a billion euros through ransomware attacks."
How does it work?
No More Ransom's goal is to help ransomware victims recover their encrypted files, raise awareness of the threat of ransomware attacks, and provide victims with easy-to-follow links to report attacks.
No More Ransom's Crypto Sheriff tool will help you find a free decryptor by uploading two encrypted files and the ransomware note, which will try to match them against a list of available tools.
If it finds a match, it shares a suitable ransomware decryptor for your encrypted files, with detailed instructions on unlocking them.
If no decryptor is found, you'll be advised to check again for a match in the future because new unlock tools are added regularly.
Europol also provides a video on how to use the Crypto Sheriff tool to recover your files without paying a ransom.
Ransomware victims are advised never to pay ransoms because that inadvertently finances future attacks but, instead, take measures to prevent and lessen the attacks' impact:
- Regularly back up data stored on your electronic devices.
- Watch your clicks – do you know where a link will take you?
- Do not open attachments in e-mails from unknown senders, even if they look important and credible.
- Ensure that your security software and operating system are up to date.
- Use two-factor authentication (2FA) to protect your user accounts.
- Limit the possibility of exfiltrating large amounts of corporate data to external file exchange portals.
- If you become a victim, do not pay! Report the crime and check No More Ransom for decryption tools.









Comments
GT500 - 2 years ago
It's only been 6 years? Seems like it's been closer to 8 years.
BH0 - 2 years ago
"Regularly back up data stored on your electronic devices."
This wont solve your problems, not only when you are big organisation. Attackers usually wait for more then half year, so all your backups are infected too. I know that, I was witness of that and its their tactics.
In the end, you will pay no matter what :)
GT500 - 2 years ago
I always recommend using a backup system that does not remain permanently connected to a computer/server. Removeable storage (USB hard drives/SSD's, tape drives, or anything else that can be quickly removed from the system once the backup process is complete) tends to be the best. NAS, SAN, and cloud backups are just sitting there waiting for a threat actor to wipe them out, and should not be entirely trusted without a secondary backup of the data they contain on some sort of removeable storage media.
BH0 - 2 years ago
GG, I agree. And I never never expose my NAS to the internet. That is simply not good idea (by my humble experience).