On December 29th, a Pastbin post was created that contains the master RSA decryption key for the FilesLocker Ransomware. The release of this key has allowed a decryptor to be created that can recover victim's files for free.
This past week, MalwareHunterTeam discovered a new "Christmas Edition" of the FilesLocker Ransomware. Like all previous versions, this variant encrypts your files, drops some ransom notes, and then demands a ransom to get your files back. In addition, it also changed your desktop wallpaper to Christmas themed background.
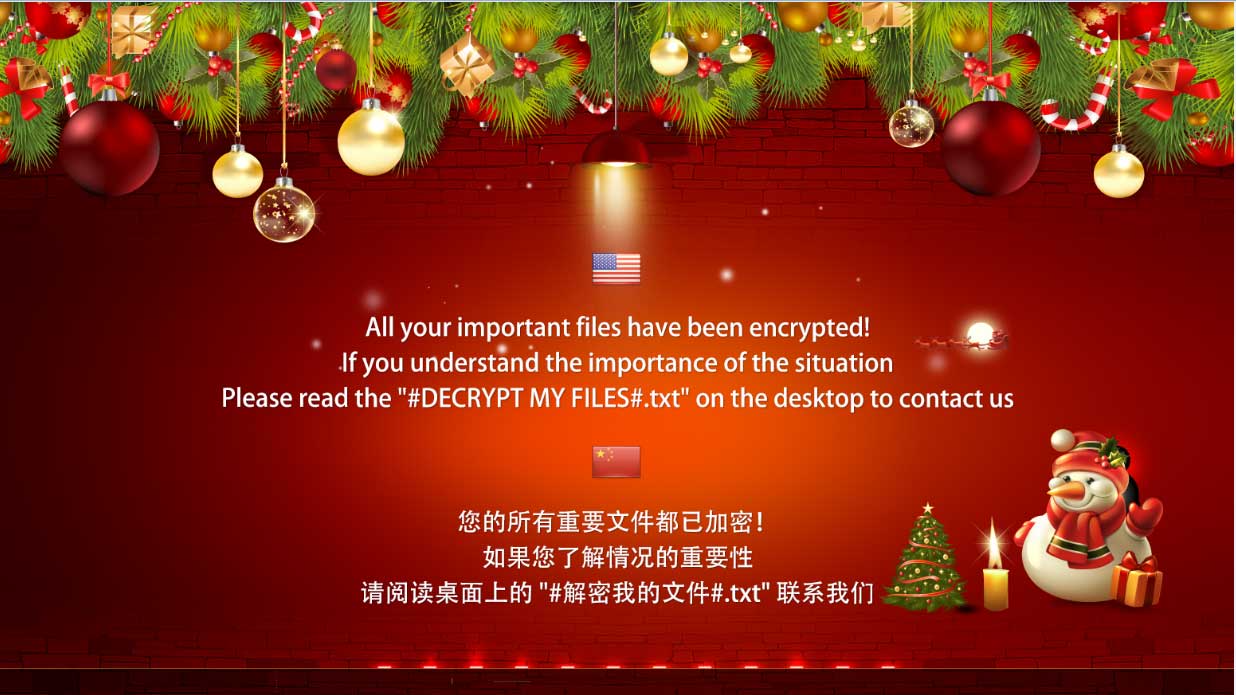
Strangely, after encrypting a victim's files, the ransomware caused a Pastebin url to be opened in your default browser that contains a message in Chinese and a RSA key. According to the message, this key is the master RSA decryption key for FilesLocker Ransomware versions 1 and 2.
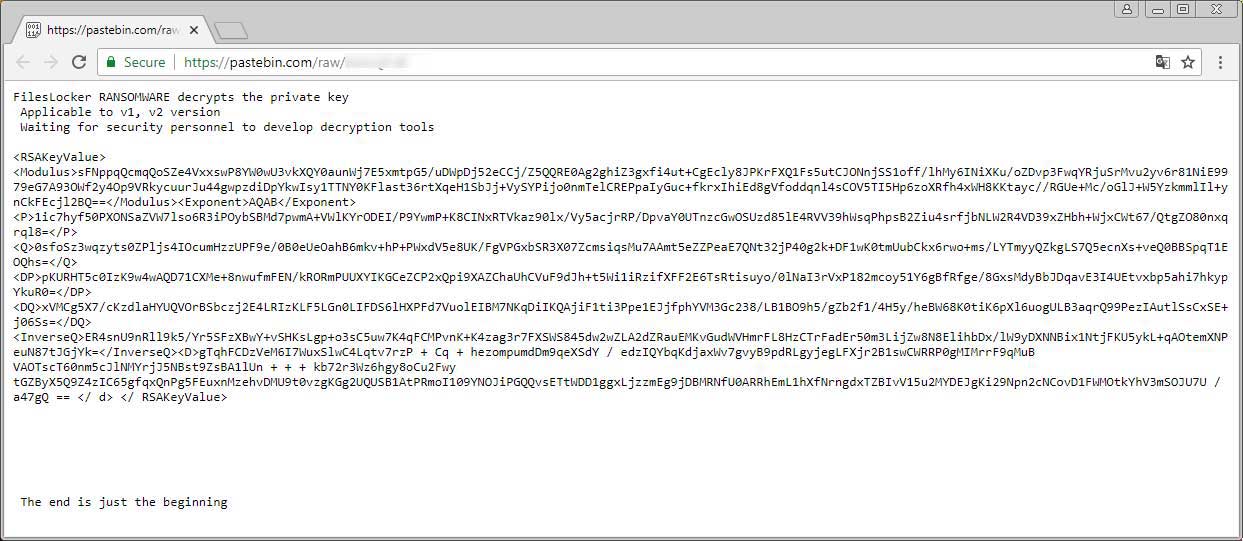
Using this key, Michael Gillespie.was able to create a decryptor that can decrypt files that have been encrypted by version 1 and 2 and that have the .[fileslocker@pm.me] extension appended to their file names. In order for the decryptor to work, the victims must load an associated ransom note into the decryptor.
These ransom notes contain an encrypted decryption key, which are then decrypted using the released master RSA private key. Full instructions on how to use this decryptor can be found here.
It is not unheard of for ransomware developers to release master keys for certain groups of people, when they switch to a new version, or decide to end their project. In this case, it is not known why the keys were released, but the final statement of "The end is just the beginning" may be a clue that they are redesigning their ransomware or switching to a new project.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now