-
How to Decrypt the FilesLocker Ransomware with FilesLockerDecrypter
On December 29th, an unknown user released the master RSA decryption key for FilesLocker v1 and v2. This allowed Michael Gillespie to release a decryptor for files encrypted by the FilesLocker Ransomware that have the .[fileslocker@pm.me] extension appended to file names.
- January 02, 2019
- 09:19 AM
 15
15
-
The Week in Ransomware - December 21st 2018 - No More Ransom
Slow week with ransomware news as we lead up into the holidays. Mostly small variants that won't get much distribution or releases of new variants of older ransomware.
- December 21, 2018
- 04:01 PM
 1
1
-
Sponsored Content

Free shadow SaaS inventory + security insightsDiscover all SaaS accounts ever created by anyone in your org, in minutes, along with insights on security risks and spend. Save time, money and effort by curbing SaaS sprawl and automating tasks like offboarding and user access reviews. Free trial.
-
How to Decrypt the Stupid Ransomware Family with StupidDecrypter
Stupid Ransomware is a family of ransomware infections that are typically utilized by less skilled developers and many utilize themes based on movies, pop-culture, or pretend to be law enforcement. This family of ransomware infections are created using an open source project that was posted to GitHub.
- December 21, 2018
- 10:17 AM
 2
2
-
How to Decrypt the InsaneCrypt or Everbe 1 Family of Ransomware
If you are infected with the InsaneCrypt or Everbe 1.0 family of ransomware infections, a decryptor has been created that recover your files for free.
- December 17, 2018
- 04:02 PM
 0
0
-
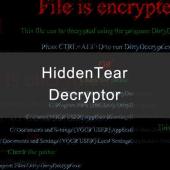
How to Decrypt HiddenTear Ransomware Variants
If you have been infected with a HiddenTear Ransomware variant, then you are in luck as a program called HiddenTearDecrypter has been created by Michael Gillespie that allows you recover your encryption key without having to pay the ransom.
- December 16, 2018
- 06:05 PM
 4
4
-
Free Decrypter Available for the Latest GandCrab Ransomware Versions
A newly released decryption tool allows free recovery of files encrypted by certain versions of GandCrab, a ransomware family that affected hundreds of thousands of people since the beginning of the year.
- October 25, 2018
- 09:04 AM
 43
43
-
Bitdefender Releases Decryption Tool for Older Version of LockCrypt Ransomware
Romanian antivirus firm Bitdefender released yesterday a decryption tool that can recover files encrypted by an older version of the LockCrypt ransomware, the one that locks files with the .1btc extension.
- July 24, 2018
- 04:43 PM
 0
0
-
Thanatos Ransomware Decryptor Released by the Cisco Talos Group
Back in February we wrote about a new ransomware called Thanatos that was encrypting victim's data, but contained flaws that would not allow the authors to decrypt a victims files even if they paid. Thankfully, the Cisco Talos Group was able to find a method to break the encryption routine.
- June 26, 2018
- 04:32 PM
 3
3
-
Decryptor Released for the Everbe Ransomware
A decryptor for the Everbe Ransomware was released by Michael Gillespie and Maxime Meignan that allows victims to get their files back for free. It is not known how this ransomware is currently being distributed, but as long as victims have an unencrypted version of an encrypted file, they can use them to brute force the decryption
- June 14, 2018
- 07:24 PM
 0
0
-
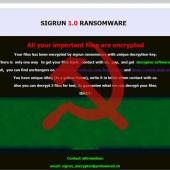
Sigrun Ransomware Author Decrypting Russian Victims for Free
The author of the Sigrun Ransomware is providing decryption for Russian victims for free, while asking for a ransom payment of $2,500 in Bitcoin or Dash for everyone else.
- June 01, 2018
- 03:35 AM
 0
0
-
Decrypters for Some Versions of Magniber Ransomware Released
Security researchers from AhnLab, a South Korea-based cyber-security firm, have created decrypters for some versions of the Magniber ransomware.
- April 03, 2018
- 05:38 AM
 0
0
-
Free Decrypter Available for GandCrab Ransomware Victims
Bitdefender has released a free decrypter that helps victims of GandCrab ransomware infections recover files without paying the ransom.
- February 28, 2018
- 05:12 AM
 7
7
-
The Week in Ransomware - February 16th 2018 - NotPetya & Saturn
The biggest news this week is the UK formally attributing NotPetya to Russian attackers. Also if interest this week is the release of the Saturn Ransomware, which has a more organized feel compared to other ransomware distributions currently being distributed
- February 16, 2018
- 04:01 PM
 1
1
-
The Week in Ransomware - February 9th 2018 - Black Ruby, GandCrab, & Decryptors
Lots of small variants released this week, but surprisingly most are actually active and being distributed. The big stories are new distribution methods for GandCrab, decryptors for Cryakl variants and MoneroPay, and a new ransomware called Black Ruby.
- February 09, 2018
- 08:30 PM
 0
0
-
Free Decryption Tool Released for Cryakl Ransomware
Belgian Federal Police together with Kaspersky Lab have released a free decryption tool for some versions of the Cryakl ransomware.
- February 09, 2018
- 05:48 AM
 5
5
-
HC7 GOTYA Ransomware Installed via Remote Desktop Services. Spread with PsExec
A new ransomware called HC7 is infecting victims by hacking into Windows computers that are running publicly accessible Remote Desktop services. Once the developers gain access to the hacked computer, the HC7 ransomware is then installed on all accessible computers on the network.
- December 06, 2017
- 04:01 PM
 1
1
-
The Week in Ransomware - December 1st 2017 - Decryptors, BTCWare, and More
It has been a busy ransomware week with lots of small and some bigger variants released. This week we had a new CryptoMix, a new BTCWare, and a few new malspam campaigns for GlobeImposter and Sigma. Even better, we had a few new and updated decryptors released so that people can recover their files for free.
- December 01, 2017
- 09:45 PM
 1
1
-
The Week in Ransomware - August 18th 2017 - SyncCrypt, GlobeImposter, & Locky
While the week was dominated by small little ransomware creations, we did have some interesting news. First, we have had a resurgence of Locky variants, then a constant stream of GlobeImposter variants variants, and finally the SynCrypt ransomware that utilizes an interesting distribution method.
- August 18, 2017
- 12:30 PM
 3
3
-
New BTCWare Ransomware Decrypter Released for the Master Variant
Security researcher Michael Gillespie has released a new version of the BTCWare ransomware decrypter after the author of the eponymous ransomware has leaked the private key for his latest version.
- July 05, 2017
- 06:00 PM
 43
43
-
The Week in Ransomware - June 2nd 2017 - XData, Decryptors, and Junkware
This has been a week of pure junk ransomware releases and decryptors. As most of these smaller ransomware variants never make it into actual distribution, I call this a win for the good guys. The big news this week is the release of the master decryption key for XData and updated an updated decryptor for Amnesia2.
- June 02, 2017
- 06:10 PM
 0
0