
Update added below about the unseizing of the data leak site and a message from the ransomware gang.
The Department of Justice announced today that the FBI successfully breached the ALPHV ransomware operation's servers to monitor their activities and obtain decryption keys.
On December 7th, BleepingComputer first reported that the ALPHV, aka BlackCat, websites suddenly stopped working, including the ransomware gang's Tor negotiation and data leak sites.
While the ALPHV admin claimed it was a hosting issue, BleepingComputer learned it was related to a law enforcement operation.
Today, the Department of Justice confirmed our reporting, stating that the FBI conducted a law enforcement operation that allowed them to gain access to ALPHV's infrastructure.
With this access, the FBI silently monitored the ransomware operation for months while siphoning decryption keys. These decryption keys allowed the FBI to help 500 victims recover their files for free, saving approximately $68 million in ransom demands.
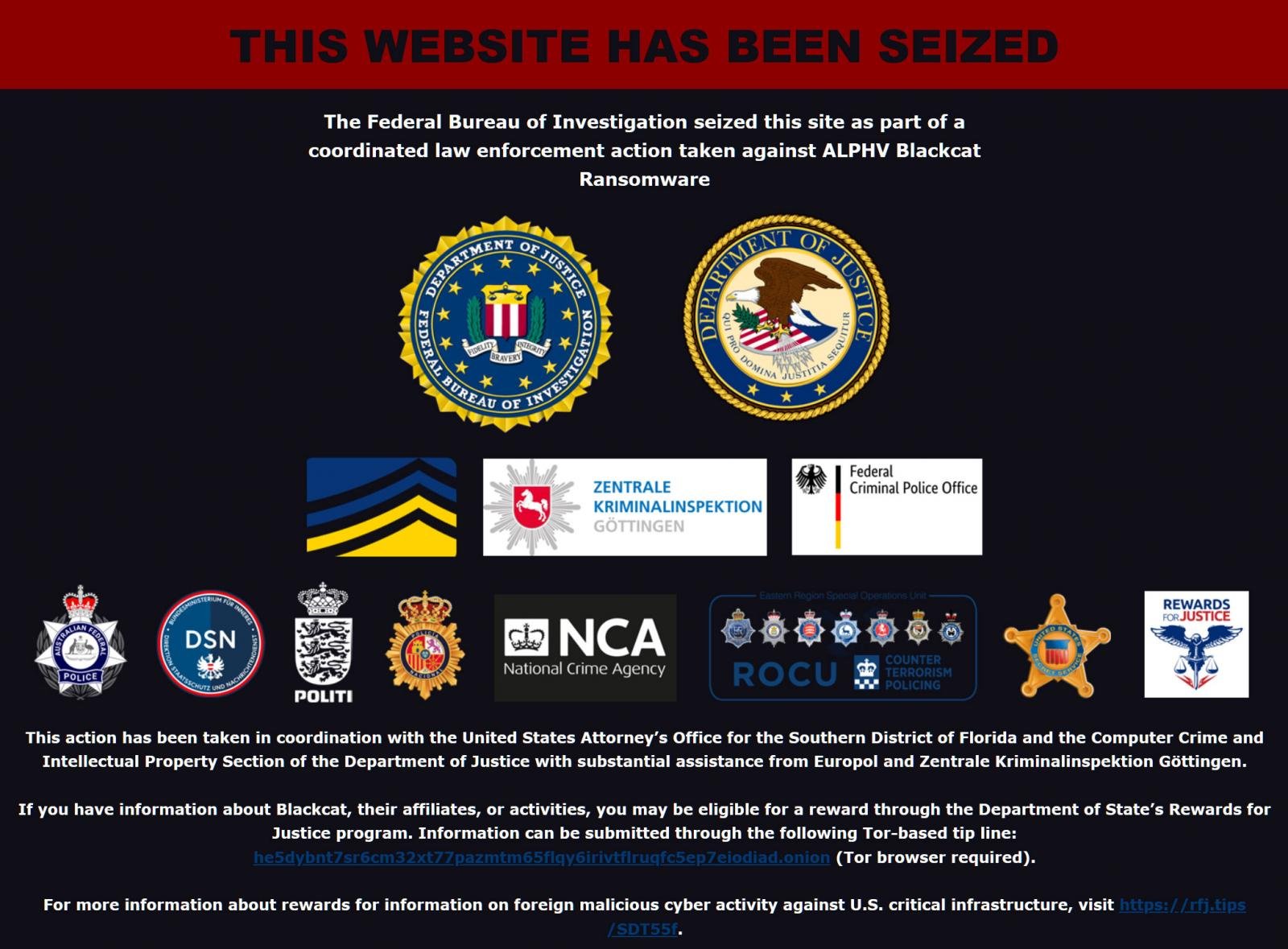
In addition, the FBI has seized the domain for ALPHV's data leak site, which now displays a banner stating that it was seized in an international law enforcement operation.
The FBI says they seized the website after obtaining the public and private key pairs for the Tor hidden services that the website operated under, allowing them to take control over the URLs.
"During this investigation, law enforcement gained visibility into the Blackcat Ransomware Group's network," reads an unsealed search warrant.
"As a result, the FBI identified and collected 946 public/private key pairs for Tor sites that the Blackcat Ransomware Group used to host victim communication sites, leak sites, and affiliate panels like the ones described above."
"The FBI has saved these public/ private key pairs to the Flash Drive."
Source: BleepingComputer.com
The seizure message states the law enforcement operation was conducted by police and investigative agencies from the US, Europol, Denmark, Germany, UK, Netherlands, Germany, Australia, Spain, and Austria.
"The Federal Bureau of Investigation seized this site as part of a coordinated law enforcement action taken against ALPHV BlackCat ransomware," reads the seizure message.
"This action has been taken in coordination with the United States Attorney's Office for the Southern District of Florida and the Computer Crime and Intellectual Property Section of the Department of Justice with substantial assistance from Europol and Zentrale Kriminalinspektion Guttingen."
Ever since the disruption to ALPHV’s servers, affiliates have been losing trust in the operation, with BleepingComputer learning that they have been contacting victims directly via email rather than using the gang’s Tor negotiation site.
This was likely due to the threat actors believing that the ALPHV infrastructure had been compromised by law enforcement, putting them at risk if they used it.
The LockBit ransomware operation has also seen this disruption as an early holiday gift, telling affiliates they can move to his operation to continue negotiating with victims.
A third breach by law enforcement
This ransomware operation has operated under multiple names over the years and has been breached by law enforcement each time.
They initially launched as DarkSide in August 2020 and then shut down in May 2021 after facing intense pressure from law enforcement operations caused by the gang's widely publicized attack on Colonial Pipeline.
The ransomware operation later returned as BlackMatter on July 31st but, once again, shut down in November 2021 after Emsisoft exploited a weakness to create a decryptor and servers were seized.
The gang returned again in November 2021, this time under the name BlackCat/ALPHV. Since then, the ransomware gang has constantly evolved its extortion tactics and taking the unusual approach of partnering with English-speaking affiliates.
However, the ransomware gang has grown increasingly toxic over the past year, posting nude photos from stolen data and aggressively calling out victims, firmly planting them in the crosshairs of law enforcement.
Like we saw in the past, due to this operation, it would not be surprising to see the ransomware gang rebrand again in the near feature under a different name.
BlackCat "unseizes" data leak site
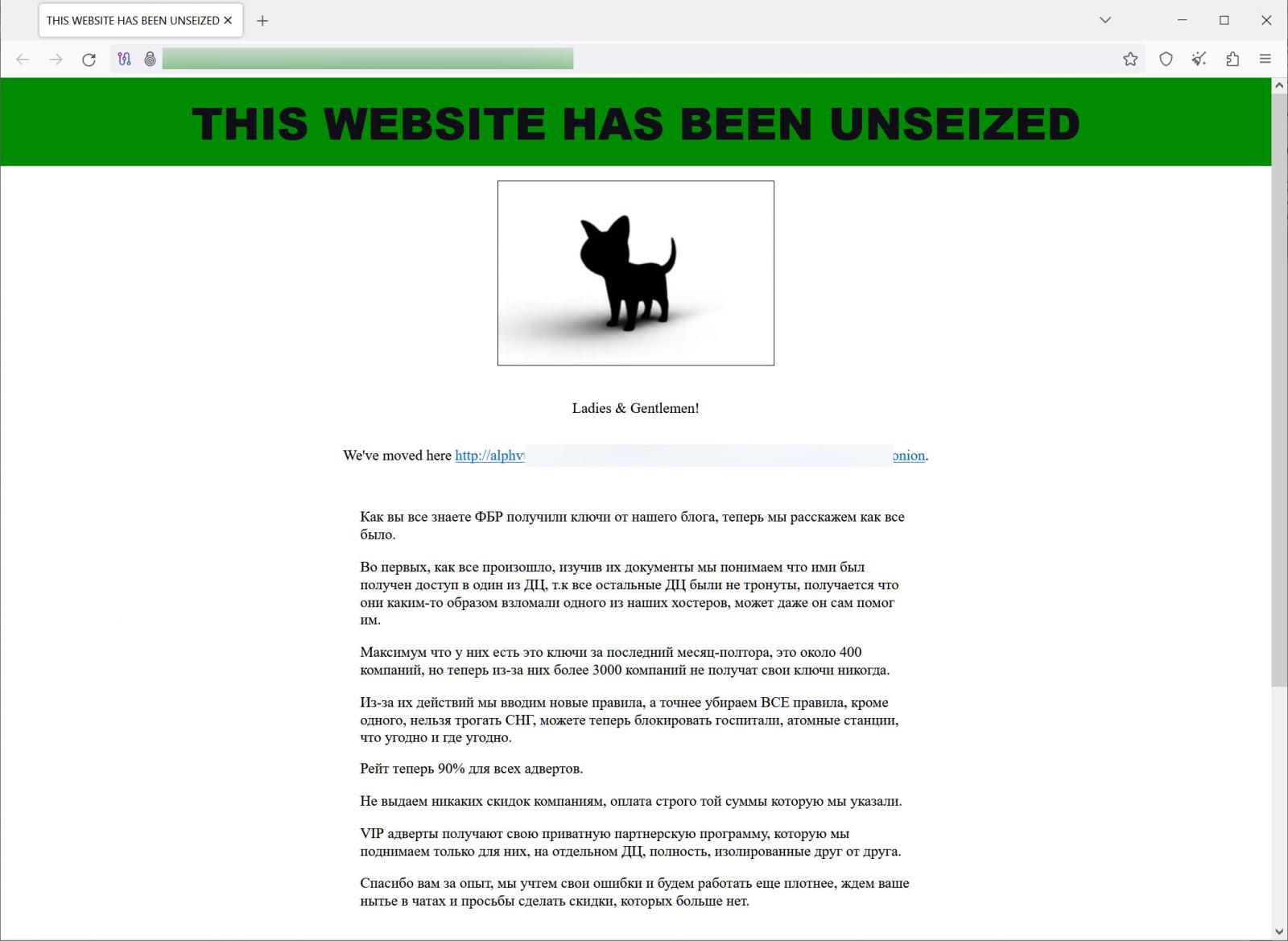
Tuesday afternoon, the ransomware operation "unseized" their data leak site to regain control of the URL and claimed that the FBI gained access to a data center they were using to host servers.
As both the ALPHV operators and the FBI now control the private keys used to register the data leak site's onion URL in Tor, they can go back and forth, seizing the URL from each other, which has been done throughout the day.
Source: BleepingComputer
As part of ALPHV's unseizure message, the gang announced the launch of a new Tor URL for their data leak site that the FBI does not have the private keys for and thus cannot seize. BleepingComputer has purposely redacted this URL from the image above.
The ransomware gang claimed that the FBI only gained access to decryption keys for the last month and a half, which is about 400 companies. However, they said 3,000 other victims will now lose their keys.
The operation also said they are removing all restrictions from their affiliates, allowing them to target any organization they wish, including critical infrastructure. Affiliates are still restricted from attacking countries in the Commonwealth of Independent States (CIS), which were previously part of the Soviet Union.
Finally, the ransomware operation has increased the affiliates revenue share to 90% of a paid ransom, likely to convince them from switching to a competing ransomware-as-service.
The full machine-translated statement is shared below:
"As you all know, the FBI got the keys to our blog, now we'll tell you how it was.
First, how it all happened, after examining their documents, we understand that they gained access to one of the DC, because all the other DC were untouched, it turns out that they somehow hacked one of our hosters, maybe even he himself helped them.
The maximum that they have is the keys for the last month and a half, it's about 400 companies, but now more than 3,000 companies will never receive their keys because of them.
Because of their actions, we are introducing new rules, or rather removing ALL the rules except one, you can not touch the CIS, you can now block hospitals, nuclear power plants, anything and anywhere.
The rate is now 90% for all adverts.
We do not give any discounts to companies, payment is strictly the amount that we specified.
VIP advertisers receive their private affiliate program, which we raise only for them, on a separate DC, completely isolated from each other.
Thank you for your experience, we will take into account our mistakes and work even harder, waiting for your whining in chat rooms and requests to make discounts that no longer exist."









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now