
Details have emerged on how the Conti ransomware gang breached the Costa Rican government, showing the attack's precision and the speed of moving from initial access to the final stage of encrypting devices.
This is the last attack from the Conti ransomware operation before the group transitioned to a different form of organization that relies on multiple cells working with other gangs.
Conti's 5-day intrusion on Costa Rica govt
The Conti ransomware operation launched in 2020 to replace Ryuk and quickly grew to infamy after attacking victims in both the private and the public sector, including local governments in the U.S., schools, and national healthcare systems.
On April 11, 2022, Conti began their last incursion under this brand after gaining initial access to the Costa Rica government’s network and engaging in reconnaissance activity.
A report from cyber intelligence company Advanced Intelligence (AdvIntel) details the Russian hackers’ steps from initial foothold to exfiltrating 672GB of data on April 15 and executing the ransomware.
The threat actor entry point was a system belonging to Costa Rica’s Ministry of Finance, to which a member of the group referred to as ‘MemberX’ gained access over a VPN connection using compromised credentials.
Advanced Intelligence CEO Vitali Kremez told BleepingComputer that the compromised credentials were obtained from malware installed on the initial device compromised on the victim network.
More than 10 Cobalt Strike beacon sessions were set up in the early stages of the attack, AdvIntel researchers say in the report.
“The infection followed a typical attack flow wherein the adversaries gained access from the compromised VPN log by installing a crypted form of Cobalt Strike inside the Costa Rica sub-network” - AdvIntel
After gaining local network domain administrator access, the intruder used the Nltest command-line tool to enumerate domain trust relationships. Next, they scanned the network for file shares using ShareFinder and AdFind utilities.
AdvIntel’s details on the threat actor’s activity on the Costa Rica government’s network include the specific commands used at each step.
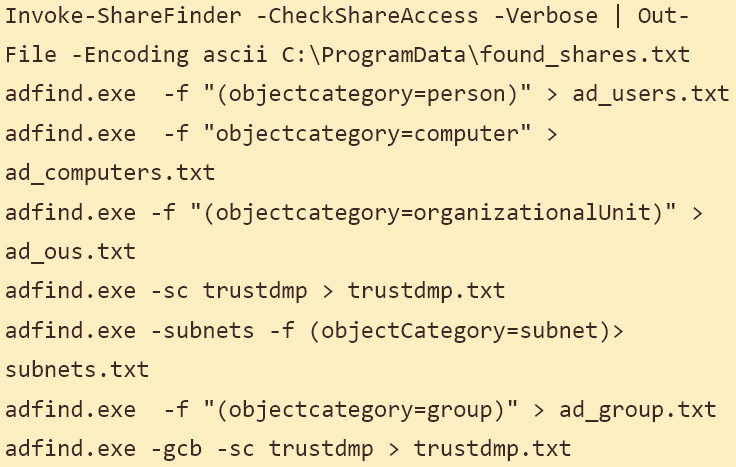
source: AdvIntel
According to the researchers, MemberX then used the Cobalt Strike backdoor channel to download the fileshare output to a local machine.
The attacker was able to access administrative shares where they uploaded a Cobalt Strike DLL beacon and then ran it using the PsExec tool for remote file execution.

source: AdvIntel
Using the Mimikatz post-exploitation tool for exfiltrating credentials, the adversary collected the logon passwords and NTDS hashes for the local users, thus getting “plaintext and bruteable local admin, domain and enterprise administrator hashes.”
The researchers say that Conti operators leveraged Mimikatz to run a DCSync and Zerologon attack that gave them access to every host on Costa Rica’s interconnected networks.
To make sure that they don’t lose access in case defenders detect the Cobalt Strike beacons, Conti planted the Atera remote access tool on hosts with less user activity where they had administrative privileges.
“The adversaries pinged the whole network and re-scanned the network domain trusts, leveraging enterprise administrator credentials with ShareFinder and compiling a list of all corporate assets and databases available under their new elevated privileges” - AdvIntel
Stealing the data was possible using the Rclone command-line program that can manage files on multiple cloud storage services. Conti used this to upload data to the MEGA file hosting service.
A diagram of the attack flow:
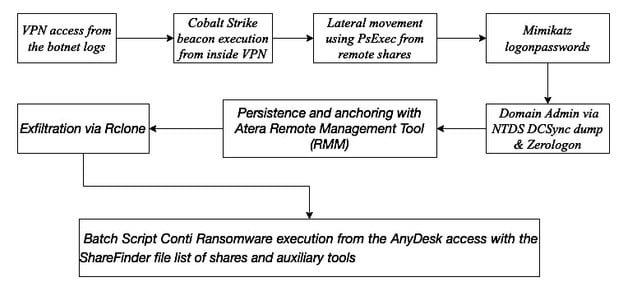
source:AdvIntel
Post-attack: national emergency, Conti shut down
According to a note on the Conti leak site, the ransom demand was initially $10 million and then increased to $20 million when Costa Rica refused to pay.
However, AdvIntel researchers say that internal communication between Conti members showed that the price “was far below $1 million USD.”
AdvIntel notes that Conti’s attack on the Costa Rican government “was relatively unsophisticated” and that a ‘flat’ network designed combined with misconfigured administrative shares helped the attacker move to domain trusts.
Following this crippling attack, Costa Rica was forced on May 8 to declare a national emergency as the intrusion had extended to multiple government bodies, with some agencies resuming activity in early June.
About 10 days later, Conti leaders started to shut down the operation by taking offline part of the infrastructure offline and announcing that the brand no longer existed.
The final step happened in late June when Conti shut down all the sites used for negotiating ransoms with victims and took offline the data leak site.
However, the cybercriminal syndicate lives on, under a different organization where its members dispersed into other ransomware operations (Quantum, Hive, AvosLocker, BlackCat, Hello Kitty).
Other operations also in the extortion business, minus the file encryption part, that are also linked to Conti are Karakurt, BlackByte, and the Bazarcall collective.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now