
MEGA has released a security update to address a set of severe vulnerabilities that could have exposed user data, even if the data had been stored in encrypted form.
MEGA is a New Zealand-based cloud storage and file hosting service with over 250 million registered users from over two hundred countries. Users have collectively uploaded a massive 120 billion distinct files amounting to 1000 petabytes in size.
One of MEGA's advertised features is that data is end-to-end encrypted, with only the user having access to the decryption key. However, researchers have shown that vulnerabilities in the encryption algorithm allowed them to access users' encrypted data.
The vulnerabilities in MEGA's encryption scheme were discovered by researchers at ETH Zurich, in Switzerland, who reported it to the firm responsibly on March 24, 2022.
While the researchers discovered five possible attacks against user data relying upon an equal number of flaws, they all rely on stealing and deciphering an RSA key.

MEGA is unaware of any compromised user accounts or data by exploiting the discovered flaws. However, this finding creates a dent in the service's data security promises.
Decrypting MEGA
MEGA uses a system of user-controlled end-to-end encryption (UCE) to protect user data even from internal access. The basis of this system is an encryption key generated from a user's regular login password.
Next, the master key is generated via a randomized process and used for the subsequent encryption of a subset of keys, including an RSA key pair, a Curve key used for chat functionality, an Ed signature key, and the Node keys.
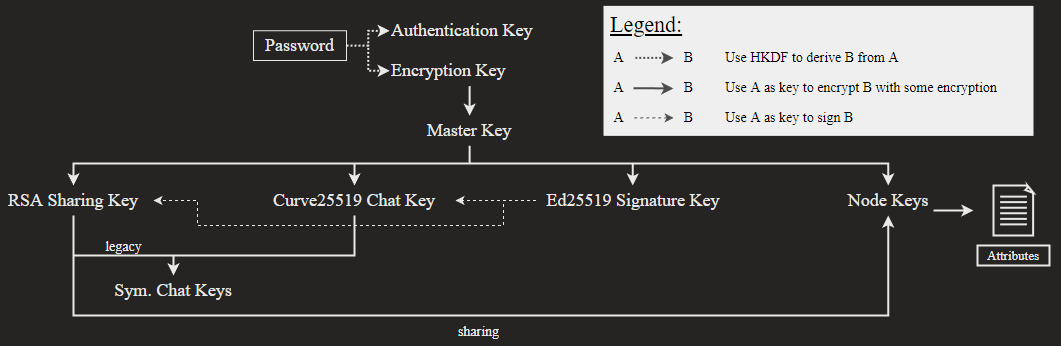
The RSA key of each user is stored on MEGA's servers with no integrity protection.
The ETH Zurich team discovered a novel way to perform a man-in-the-middle attack that can recover the RSA keys of targeted MEGA accounts. The researchers also released the following proof-of-concept video:
This attack relies upon prime factor guessing through comparison and requires at least 512 login attempts to work. Moreover, the adversary would have to access MEGA's servers to carry out the attack.
This is highly complicated and generally difficult for outsider threats, but it wouldn't be as challenging for rogue/unethical MEGA employees.
Once a targeted account's RSA key leaks the user's ciphertexts, the attacker can work backward to recover the AES-ECB of the master key in plaintext and then decrypt the entire key subset.
Eventually, the attacker can decrypt user data stored on the MEGA cloud, access chats in cleartext form, and even upload new content to the account's repository.
Remedy and implications
MEGA has fixed the two vulnerabilities that can lead to user data decryption on all clients (RSA key recovery and plaintext recovery), mitigated a third one (framing), and plans to address the remaining two of the discovered issues in upcoming updates.
The fixes aren't perfect countermeasures, but they don't impact user experience and don't require users to re-encrypt their stored data, change their password, or create new keys.
The cloud service provider claims that there are no signs of user accounts or data being accessed inappropriately, either from insiders or outsiders.
"Seeing how seemingly innocuous cryptographic design shortcuts taken almost a decade ago backfire under scrutiny by three of the sector's brightest minds is both frightening and intellectually fascinating," comments MEGA on the findings.
"The very high threshold of exploitability, despite the broad range of identified cryptographic flaws, provides a certain sense of relief."
Despite the assurances by MEGA that no data was compromised, the research has effectively nullified MEGA's data confidentiality assurances that differentiated them from their competition for over a decade.









Comments
Sgtkeebler - 2 years ago
I was reading the security group or individuals who reported this won't greelight this fix because even though they can't exploit Mega using their proof-of-concept it still looks like their are other ways this can be exploited.