
Researchers have conducted a technical experiment, testing ten ransomware variants to determine how fast they encrypt files and evaluate how feasible it would be to timely respond to their attacks.
Ransomware is malware that enumerates the files and directories on a compromised machine, selects valid encryption targets, and then encrypts the data, so it is unavailable without a corresponding decryption key.
This prevents the data owner from accessing the files, so ransomware attacks are either carried out for data destruction and operational disruption or financial extortion, demanding the payment of a ransom in return for a decryption key.
How fast a device is encrypted is important, as the quicker it is detected, the less damage is done, and the volume of data needing to be restored is kept to a minimum.
Putting ransomware to the test
Researchers at Splunk conducted 400 encryption tests, consisting of 10 different families, ten samples per family, and four different host profiles reflecting different performance specifications.
"We created four different "victim" profiles consisting of Windows 10 and Windows Server 2019 operating systems, each with two different performance specifications benchmarked from customer environments," Splunk explained in their report.
"We then chose 10 different ransomware families and 10 samples from each of those families to test."
During these tests, the researchers evaluated the encryption speed against 98,561 files totaling 53GB using various tools, such as native Windows logging, Windows Perfmon statistics, Microsoft Sysmon, Zeek, and stoQ.
The host system hardware and OS configurations varied to reflect a realistic corporate network setting, and the analysts measured all encryption times and derived the median speed of encryption for each variant.
The total median time for all 100 different samples of the ten ransomware strains on the test rigs was 42 minutes and 52 seconds.
However, as reflected in the following table, some ransomware samples deviated significantly from this median value.
.jpg)
The "winner," and the most lethal strain in response time margins was LockBit, achieving an average of 5 minutes and 50 seconds. The fastest LockBit variant encrypted 25,000 files per minute.
LockBit has long bragged on their affiliate promotion page that they are the fastest ransomware for encrypting files, releasing their own benchmarks against over 30 different ransomware strains.
The once-prolific Avaddon achieved an average of just over 13 minutes, REvil encrypted the files in about 24 minutes, and BlackMatter and Darkside completed the encryption in 45 minutes.
On the slower side, Conti needed almost an hour to encrypt the 54 GB of test data, while Maze and PYSA finished in nearly two hours.
The time factor
While time is an important factor, it's not the only detection opportunity in ransomware attacks, which typically involve reconnaissance periods, lateral movement, credential-stealing, privilege escalation, data exfiltration, disabling of shadow copies, and more.
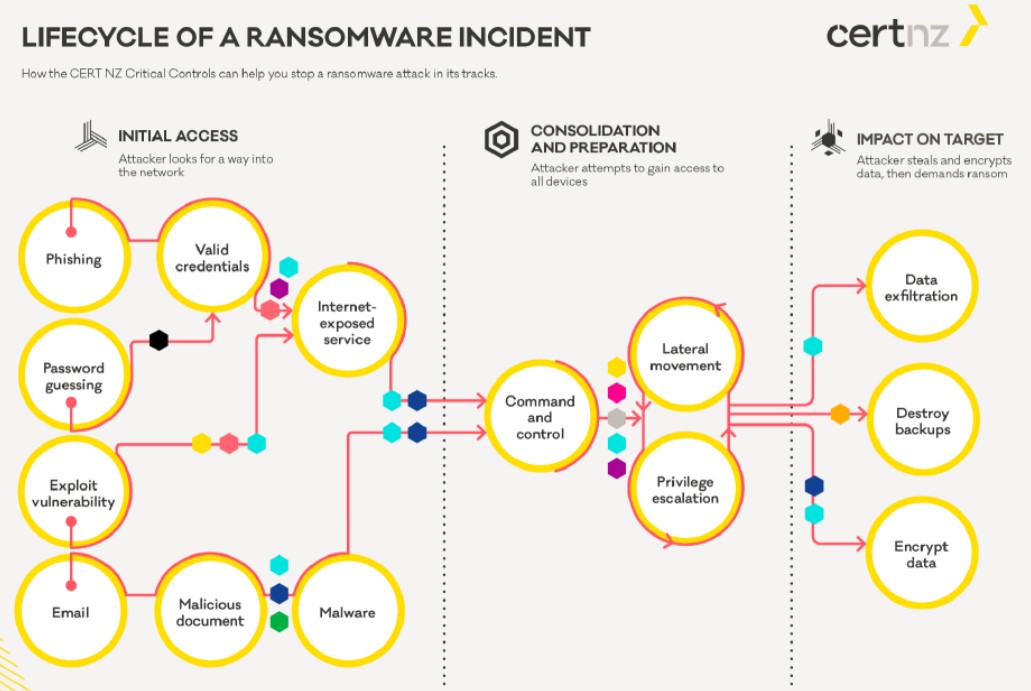
After the encryption is over, it is the strength of the encryption scheme itself that determines how long-lasting or manageable the consequences of the attack will be, so strength is more important than speed.
The short time to respond when ransomware is ultimately deployed highlights that focusing on that particular detection and mitigation opportunity is unrealistic and ultimately wrong.
As noted in the Splunk report, this research demonstrates the need for organizations to shift focus from incident response to ransomware infection prevention.
The overall median of 43 minutes is a tiny window of opportunity for network defenders to detect ransomware activity, considering that previous studies have found that the average time to detect compromise is three days.
Since most ransomware groups hit during weekends when the IT teams are understaffed, most encryption attempts are completed successfully, so the time for encryption shouldn't be a significant consideration for defenders.
Ultimately the best defense is to detect unusual activity during the reconnaissance stage, before ransomware is even deployed.
This includes looking for suspicious network activity, unusual account activity, and the detection of tools commonly used before an attack, such as Cobalt Strike, ADFind, Mimikatz, PsExec, Metasploit, and Rclone.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now