Users of QNAP network-attached storage (NAS) devices are reporting attacks on their systems with the eCh0raix ransomware, also known as QNAPCrypt.
The threat actor behind this particular malware intensified their activity about a week before Christmas, taking control of the devices with administrator privileges.
Attack count jumps before Christmas
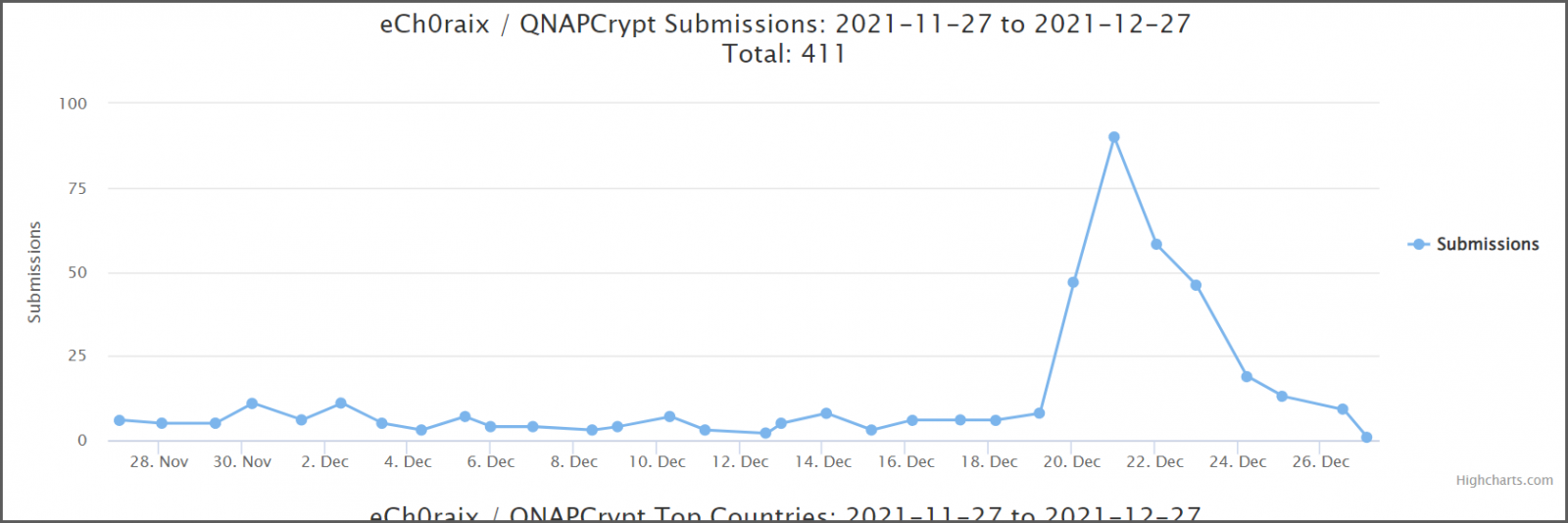
BleepingComputer forum users managing QNAP and Synology NAS systems have been regularly reporting eCh0raix ransomware attacks but more of them started to disclose incidents around December 20.
The jump in the number of attacks is confirmed by the ID ransomware service, where submissions started to increase on December 19 and subsided towards December 26.
The initial infection vector remains unclear at the moment. Some users admit they were reckless and did not secure the device properly (e.g. expose it to the internet over an insecure connection); others claim a vulnerability in QNAP’s Photo Station allowed the attackers to wreak havoc.
Yes I know I am a total idiot for leaving that open to this type of hack but I didnt take any of that seriously. I always thought no-one want the little guy and I will be the first to say I was wrong!
Regardless of the attack path, it appears that the eCh0raix ransomware actor creates a user in the administrator group, which allows them to encrypt all files on the NAS system.
QNAP users - some of them using the NAS device for business purposes - reported on the BleepingComputer forum that the malware encrypted pictures and documents.
Apart from the spike in the number of attacks, what stands out in this campaign is that the actor mistyped the extension for the ransom note and used the “.TXTT” extension.
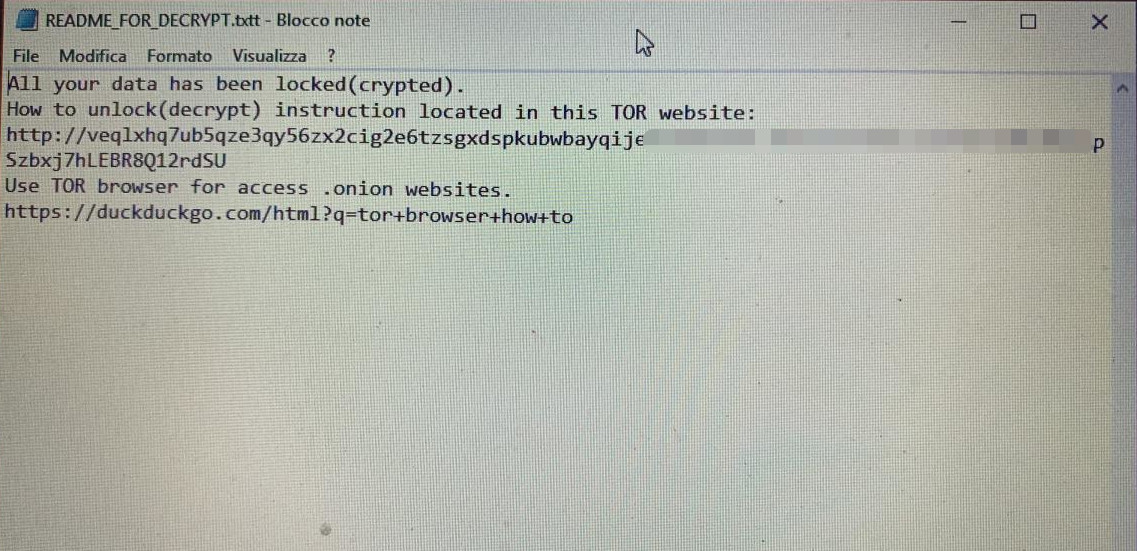
While this does not prevent viewing the instructions, it may create a problem for some users, who will have to point the operating system to open the file with a specific program (e.g. Notepad) or load it in said program.
BleepingComputer has seen ech0raix ransomware demands ranging from .024 ($1,200) to .06 bitcoins ($3,000) during these recent attacks.. Some users had no backup options and had to pay the threat actor to recover their files.
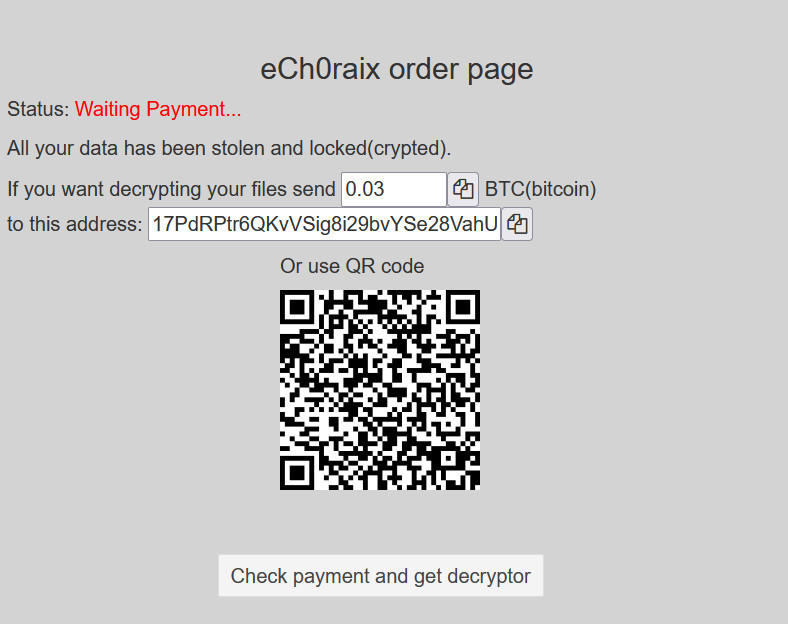
It is important to note that there is a free decryptor for files locked with an older version (before July 17th, 2019) of eCh0raix ransomware. However, there is no free solution to decrypt data locked by the latest variants of the malware (versions 1.0.5 and 1.0.6).
Attacks with eCh0raix/QNAPCrypt started in June 2019 and have been a constant threat ever since. QNAP earlier this year alerted its users of another flurry of eCh0raix attacks earlier this year, targeting devices with weak passwords.
Users should follow QNAP's recommendations to ensure proper protection of their NAS devices and the data they store.









Comments
Shplad - 2 years ago
I thought there was a fix/patch for this vulnerability months ago?
Or is this only happening to people who never applied the patch?
carlafilomena - 1 year ago
Ainda não existe um descodificador para ataques deste ransomware eCh0raix mais recente?