
The National Security Agency (NSA) has shared guidance on how to detect and replace outdated Transport Layer Security (TLS) protocol versions with up to date and secure variants.
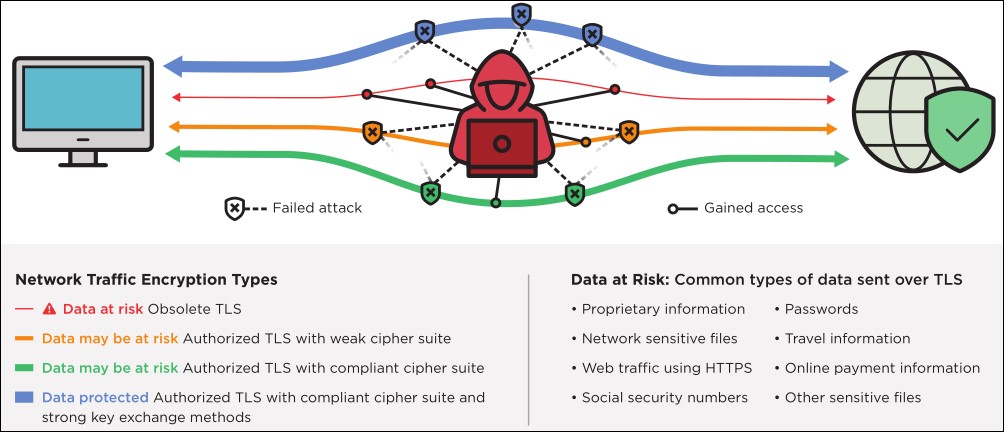
The US intelligence agency also highlights the dangers behind using deprecated TLS including both risks of sensitive data exposure and decryption of network traffic in man-in-the-middle attacks.
"Remediation is crucial to decreasing computer system and network attack surfaces and preventing unauthorized access to private data," the agency said.
"NSA recommends that only TLS 1.2 or TLS 1.3 be used and that SSL 2.0, SSL 3.0, TLS 1.0, and TLS1.1 not be used."
Implementing the measures in NSA's guidance eliminates the false sense of security provided by obsolete encryption protocols by helping block insecure TLS versions, cipher suites, and key exchange methods to properly encrypt network traffic.
Updating TLS configurations will provide government and enterprise organizations with stronger encryption and authentication to help them build a better defense against malicious actors' attacks and protect important information.
NSA's guidance is targeted at National Security System (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB) cybersecurity leaders, as well as network security analysts and system administrators.
The tools, network signatures, and server configurations shared today by the NSA are designed to help government network owners enhance their cybersecurity posture by allowing only authorized and strong encryption protocol configurations in their orgs' environments.
However, since the risks stemming from deprecated TLS protocols' weak encryption affect all networks, the guidance should be followed by all "network owners and operators" who want to decrease their risk exposure and harden their systems against attacks using these attack vectors.
"Obsolete configurations provide adversaries access to sensitive operational traffic using a variety of techniques, such as passive decryption and modification of traffic through man-in-the-middle attacks," the NSA said.
"Attackers can exploit outdated transport layer security (TLS) protocol configurations to gain access to sensitive data with very few skills required."
The Cybersecurity Information Sheet released today by the NSA [PDF] provides extensive information for all network administrators on deprecated TLS versions, cipher suites, and key exchange mechanisms, as well as on recommended TLS configs, detection strategy, and remediation.
Microsoft, Google, Apple, and Mozilla said in a coordinated announcement from October 2018 that they will be retiring the insecure TLS 1.0 and TLS 1.1 protocols starting with the first half of 2020.
Microsoft has enabled TLS 1.3 by default in the latest Windows 10 Insider builds starting with August 2020.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now