
When a company suffers a ransomware attack, many victims feel that the attackers quickly deploy the ransomware and leave so they won't get caught. Unfortunately, the reality is much different as threat actors are not so quick to give up a resource that they worked so hard to control.
Instead, ransomware attacks are conducted over time, ranging from a day to even a month, starting with a ransomware operator breaching a network.
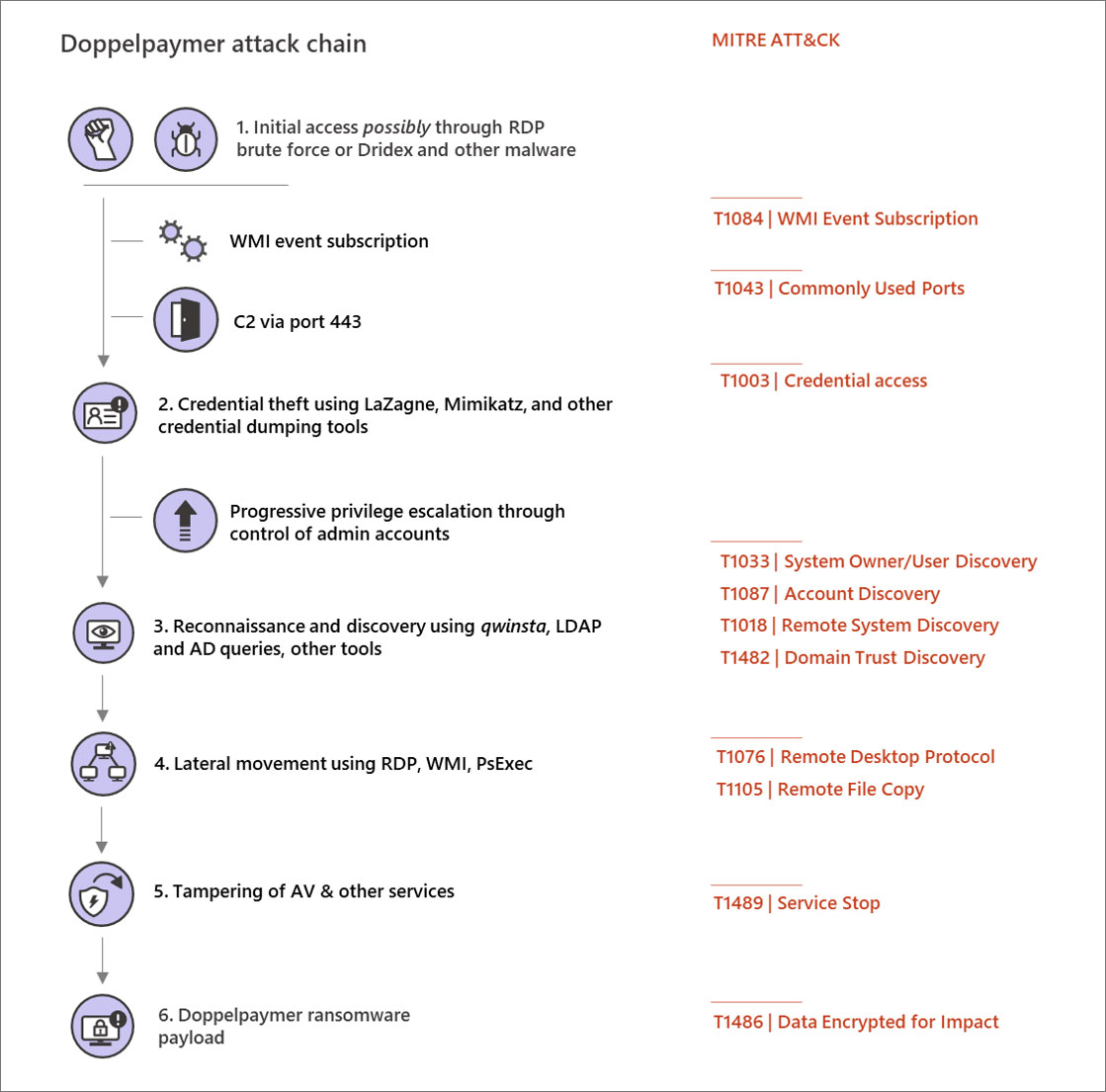
This breach is through exposed remote desktop services, vulnerabilities in VPN software, or via remote access given by malware such as TrickBot, Dridex, and QakBot.
Once they gain access, they use tools such as Mimikatz, PowerShell Empire, PSExec, and others to gather login credentials and spread laterally throughout the network.
Source: Microsoft
As they gain access to computers on the network, they use these credentials to steal unencrypted files from backup devices and servers before deploying the ransomware attack.
Once the ransomware is deployed, many victims have told BleepingComputer that while their network is still compromised, they think the ransomware operators are now gone from the system.
This belief is far from the truth, as illustrated by a recent attack by the Maze Ransomware operators.
Maze kept stealing files after the ransomware attack
Recently, the Maze Ransomware operators disclosed on their data leak site that they had hacked into the network of a subsidiary for ST Engineering named VT San Antonio Aerospace (VT SAA).
What's creepy about this leak is that Maze leaked a document containing the victim's IT department report on their ransomware attack.

This stolen document shows that Maze was still lurking on their network and continued to spy on steal files from the company as an investigation into the attack continued.
This continued access is not uncommon when it comes to these types of attacks.
John Fokker, Principal Engineer and Head of Cyber Investigations for McAfee, told BleepingComputer that in some attacks, the threat actors were reading victim's emails even as ransomware negotiations were taking place.
"We know of several cases where Ransomware actors remained on a victim's network after they have deployed their ransomware. In these cases, the attackers encrypted the victim's backups after the initial attack or during negotiations, which made it clear that the attacker still had access and was reading the victim's email."
Advice from the experts
After detecting a ransomware attack, the first step a company should do is shut down their network and the computers running on it. These actions prevent the continued encryption of data and deny access to the system for the attackers.
Once this is done, a third-party cybersecurity company should be brought in to perform a full investigation of the attack and audit of all internal and public-facing devices.
This audit includes analyzing the corporate devices for persistent infections, vulnerabilities, weak passwords, and malicious tools left behind by the ransomware operators.
In many cases, the remediation and investigation are covered by a victim's cyber insurance policy.
Fokker and Vitali Kremez, Chairman of Advanced Intel, also offered some additional advice and strategies that should be taken to remediate an attack properly.
"The larger corporate ransomware attacks almost always involve a complete compromise of a victim's network from backup servers to Domain controllers. By having complete control of a network, Ransomware actors can easily turn off defenses and deploy their ransomware."
"Incident Response (IR) teams faced with such a far going intrusion need to assume that the attacker is still in the network till proven otherwise. This means first and foremost choosing a different communication channel (not visible to the threat actor) to discuss the ongoing IR efforts."
"It is important to note is that attackers already have been ploughing around in a victim's Active Directory so in order to flush out any remaining backdoor accounts a full AD review needs to be undertaken," Fokker explained to BleepingComputer.
Kremez also suggested a separate secure communications channel as well as a walled-off storage channel that can be used to store data related to the investigation.
"Treat ransomware attacks as data breach incidents with the hypothesis that the attackers might still be inside the network. Therefore, victims should work from the bottom-up trying to obtain forensics evidence that validates or invalidates the hypothesis. It often includes a full forensic sweep of the network infrastructure with the focus on the privileged accounts. Make sure to have a business continuity plan to have a separate secure communication and storage channel (separate infrastructure) while doing the forensics assessment," Kremez told us.
Kremez noted that reimaging the devices on a compromised network is suggested, but may not be enough as the attackers likely have full access to network credentials that can be used for another attack.
"Victims should potentially reinstall the machines and servers. However, they should be mindful the criminal might have already stolen the credentials. Simply reinstalling might not be enough. They would also need to change the domain passwords as the criminals might come back using such credentials," Kremez continued.
Ultimately, it is essential to operate under the assumption that even after an attack, the attackers are likely to be still watching a victim's movements.
This spying could not only hamper a breached network's cleanup but could also affect negotiation tactics as the attackers read a victim's email and stay one step ahead.









Comments
Nighthawke1701b - 4 years ago
This has been known for some time. I've experienced break-ins and squatting on more than one network that was cleansed, but not secured. And believe me, they like their turf when they find it. It takes some serious work to evict them and make that network secure from their prying eyes.