
Security researchers have released details about two vulnerabilities in the Western Digital and SanDisk SSD Dashboard application that could be exploited to trick users into running arbitrary code on their computers.
Both applications are utility kits that help users monitor the performance of their SSDs, as well as diagnose problems and collect troubleshooting information.
The packages come with tools for SSD firmware updates and for reading drive details (model, capacity, SMART attributes).
Easy man-in-the-middle attack
A hacker could exploit the two vulnerabilities in a man-in-the-middle (MitM) attack to steal system information reports or to serve malware by triggering an application update.
The most severe of the flaws is the use of the insecure HTTP for communicating with Dashboard's web service, security researcher Martin Rakhmanov from Trustwave found.
"Using a network capture running on the same computer as the app, it was clear that the application uses HTTP instead of HTTPS for communication with SanDisk site"
When Dashboard makes a request for available updates it receives an XML file with the latest version number available for the utility.
If the XML file shows a version number higher than the current installation, the application downloads and installs it from the included URL, without verifying the package.
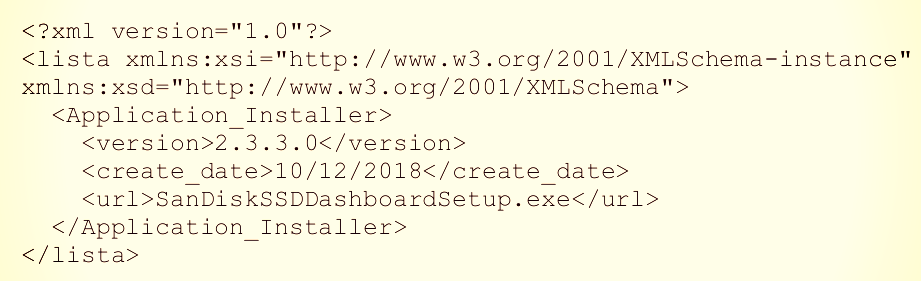
An attacker intercepting the update request could change the release version, which triggers the update process. By providing an IP address for the hosing server, an attacker could push malware to the victim's system and execute it.
"The use of HTTP makes it susceptible to man-in-the-middle attacks. Leveraging a rogue hotspot, an attacker could direct a computer using the SanDisk app to join the network then serve it malicious content." says Martin Rakhmanov, Trustwave
This vulnerability has been assigned the identification number CVE-2019-13467 and affects Western Digital and SanDisk SSD Dashboard applications prior to version 2.5.1.0. The fix from the manufacturer consists of switching the update service to HTTPS.
Encrypting data for naught
Less severe in nature, the second security bug (CVE-2019-13466) is a hardcoded password intended to encrypt the customer reports that users send to support staff for examination.
Rakhmanov found the bug after dumping strings from the main binary file - SanDiskSSDDashboard.exe.
One of the strings caught his eye and prompted an investigation into where it was used. It turned out that the string was a hardcoded password used for encrypting report information.
"C:/Program Files (x86)/SanDisk/SSD Dashboard/7za.exe" a -tzip
"C:/SSD_Dashboard_Report.zip"
"C:/Users/martin/Desktop/SSD_Dashboard_Report_msinfo.txt"
"C:/SSD_Dashboard_Report_msinfo.txt" -pS@nD!sk.1
The password is the same for every installation, so an attacker intercepting the report could read all the data included, which could be personally identifying information or some other type of confidential details.
In an advisory published earlier this month, Western Digital informs that the problem was solved by dropping encryption for the reports and forcing users in need of support to submit report data to share it directly with the company's staff doing customer support.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now