
Threat actors trying to steal your credentials through phishing attackers is nothing new, and the number of campaigns has only been rising in recent times.
Government estimates indicate that phishing is a multi-billion dollar industry, which is why cybersecurity companies exist that focus entirely on securing client's inboxes from malicious email.
Due to this, attackers continuously come up with new tricks to bypass secure email gateways, such as foreign languages, CSS tricks, specially crafted ZIP files, and hacked SharePoint sites.
This week, however, we learned of a new strand of Bank of America phishing emails making their way through to Outlook inboxes. These emails bypassed security controls despite there being enough clues that they are part of a phishing attack.
Doing things differently helped bypass filters
In a report shared with BleepingComputer, email security company Armorblox details a recent Bank of America phishing campaign that was able to bypass email gateways.
Armorblox recently caught a phishing attempt that landed in the mailboxes of some of its customers.
"This email claimed to come from Bank of America and asked readers to update their email address. Clicking the link took the targets to the credential phishing page resembling the Bank of America home page, designed to make targets part with their account credentials. The attack flow also included a page that asked readers for their ‘security challenge questions’, both to increase legitimacy as well as get further identifying information from targets," ArmorBlox's report explained.
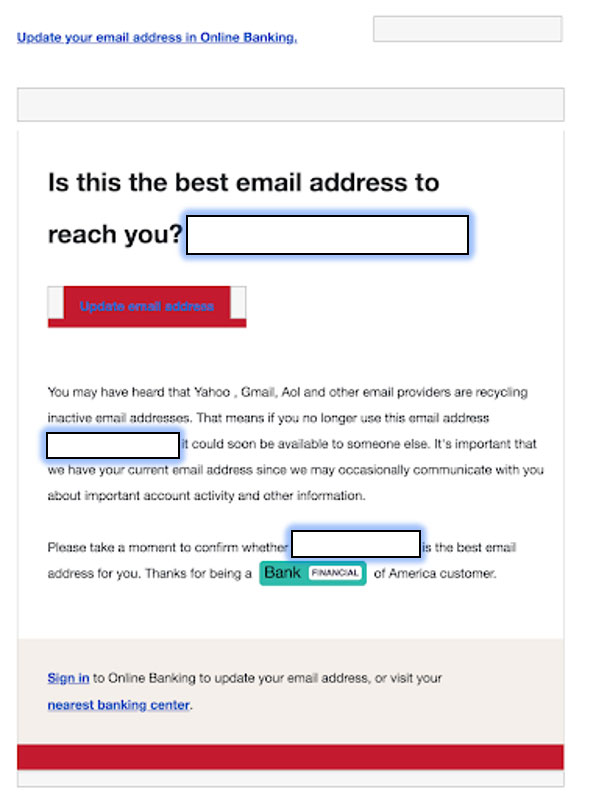
Source: ArmorBlox
As the email originated from a "@yahoo.com" email address, any tech-savvy user paying attention should be able to tell this is a classic case of phishing. Then why did advanced filtering technologies miss it?
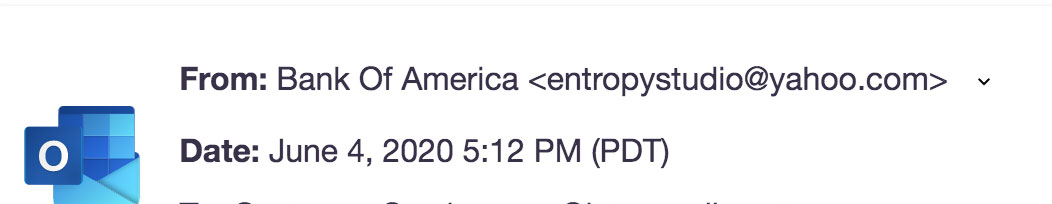
Source: ArmorBlox
ArmorBlox cofounder Chetan Anand shined some light on the matter here:
"This email got past existing email security controls because it didn’t follow the tenets of more traditional phishing attacks."
Anand noted that this was not a mass email but targeted only a few people in the organization. This low volume enabled it to slip past Microsoft’s email security and Secure Email Gateway (SEG), whose defense may trigger when seeing a large volume of similar email.
Secondly, the phishing email passed all of the security checks: "Although the sender name - Bank of America - was impersonated, the email was sent from a personal Yahoo account via SendGrid," said Anand. "This resulted in the email successfully passing all authentication checks such as SPF, DKIM, and DMARC."
Technologies like SPF, DKIM, and DMARC help verify if an email has been sent from the domain it claims to be originating from, and that its integrity hasn't been compromised.
In this case, the email did indeed originate from the Yahoo Account it claimed to be coming from. These technologies do not and cannot check the validity of the Sender’s Name. To SPF, DKIM, or DMARC programs, the sender name being "Bank of America" or "John Smith" doesn't mean anything; it’s irrelevant.
Finally, the email body didn’t contain any domains which could yet be recognized as malicious. This is because of, what Armorblox called "zero-day link and look alike website."
The phishing domain nulledco[.]store had only been registered on June 1st and had a valid COMODO SSL certificate assigned to it. No security databases and online scan engines (such as VirusTotal) had flagged it as malicious just yet.
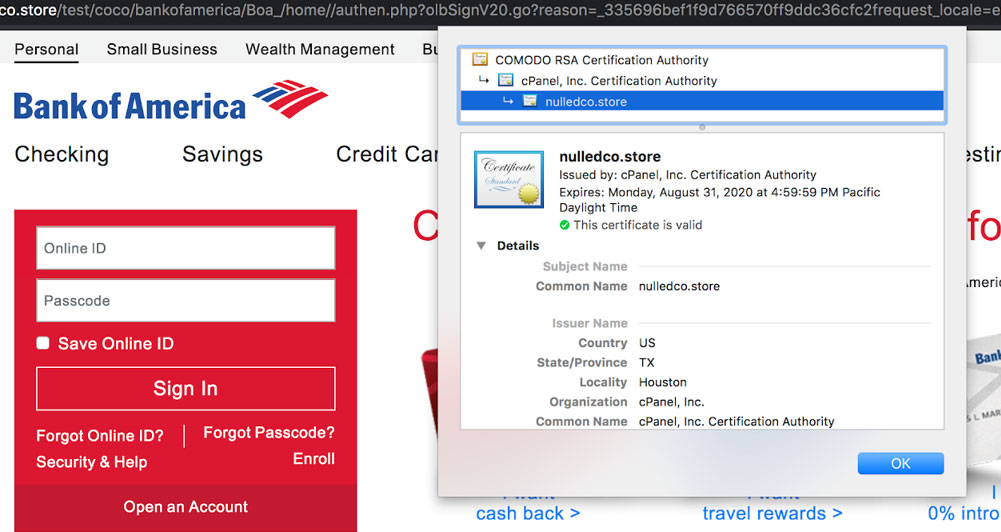
Source: ArmorBlox
Furthermore, there were elements of social engineering carefully embedded within the crafted email. "The email language and topic was intended to induce urgency in the reader owing to its financial nature. Asking readers to update the email account for their bank lest it get recycled is a powerful motivator for anyone to click on the URL and follow through," stated the company.
To spot this email, instead of relying on the usual security controls, Armorblox states it is necessary to look at other factors.
These factors include the language and tone of the email, signs of brand impersonation, prior communication history of the sender with the recipient (rather, lack thereof), and the domain frequency.
When trying to detect these factors, machine learning and artificial intelligence algorithms may be better suit as they can build large datasets to compare them.
With an increase in the number of phishing campaigns being sent out every day, machine-learning and AI-powered approaches may promise superior results than traditional email monitoring technologies.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now