.jpg)
A new version of the Android spyware 'Mandrake' has been found in five applications downloaded 32,000 times from Google Play, the platform's official app store.
Bitdefender first documented Mandrake in 2020, with the researchers highlighting the malware's sophisticated spying capabilities and noting that it has operated in the wild since at least 2016.
Kaspersky now reports that a new variant of Mandrake that features better obfuscation and evasion sneaked into Google Play through five apps submitted to the store in 2022.
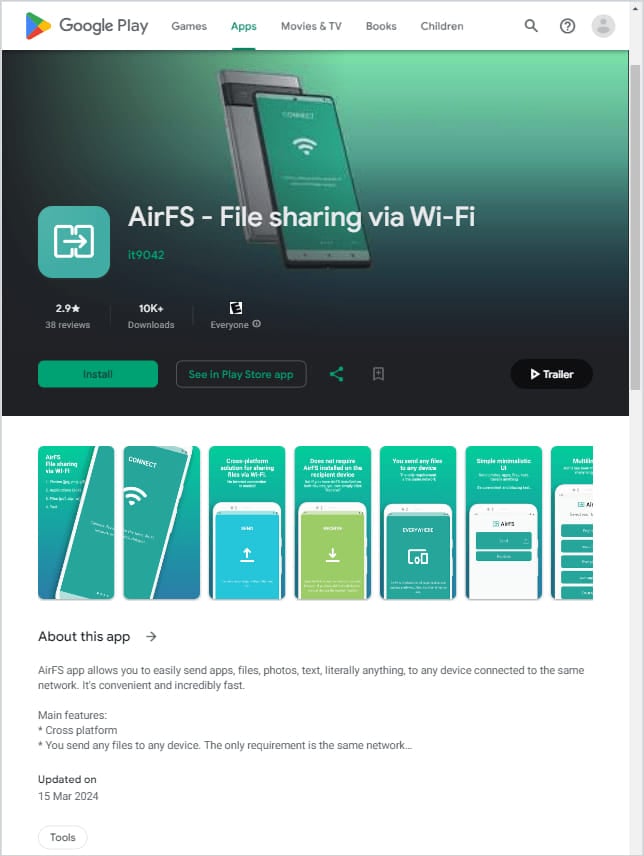
Those apps remained available for at least a year, while the last one, AirFS, which was the most successful in terms of popularity and infections, was removed at the end of March 2024.
Source: Kaspersky
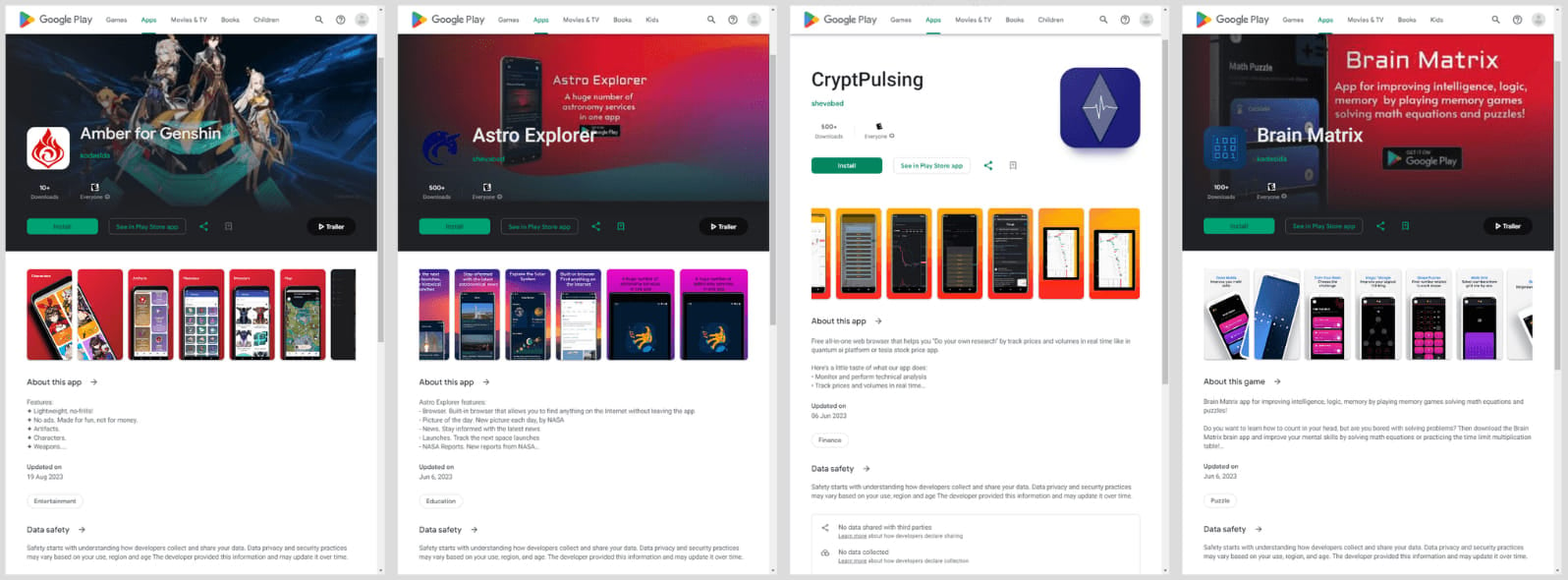
Kaspersky identified the five Mandrake-carrying apps as follows:
- AirFS – File sharing via Wi-Fi by it9042 (30,305 downloads between April 28, 2022, and March 15, 2024)
- Astro Explorer by shevabad (718 downloads from May 30, 2022 to to June 6, 2023)
- Amber by kodaslda (19 downloads between February 27, 2022, and August 19, 2023)
- CryptoPulsing by shevabad (790 downloads from November 2, 2022, to June 6, 2023)
- Brain Matrix by kodaslda (259 downloads between April 27, 2022 and June 6, 2023)
The cybersecurity firm says most downloads come from Canada, Germany, Italy, Mexico, Spain, Peru, and the UK.
Source: Kaspersky
Evading detection
Unlike typical Android malware, which places malicious logic in the app's DEX file, Mandrake hides its initial stage in a native library, 'libopencv_dnn.so,' which is heavily obfuscating using OLLVM.
Upon the malicious app's installation, the library exports functions to decrypt the second-stage loader DEX from its assets folder and load it into memory.
The second stage requests permissions to draw overlays and loads a second native library, 'libopencv_java3.so,' which decrypts a certificate for secure communications with the command and control (C2) server.
Having established communication with the C2, the app sends a device profile and receives the core Mandrake component (third stage) if deemed suitable.
Once the core component is activated, Mandrake spyware can perform a wide range of malicious activities, including data collection, screen recording and monitoring, command execution, simulation of user swipes and taps, file management, and app installation.
Notably, the threat actors can prompt users to install further malicious APKs by displaying notifications that mimic Google Play, hoping to trick users into installing unsafe files through a seemingly trusty process.
Kaspersky says the malware also uses the session-based installation method to bypass Android 13's (and later) restrictions on the installation of APKs from unofficial sources.
Like other Android malware, Mandrake can ask the user to grant permission to run in the background and hide the dropper app's icon on the victim's device, operating stealthily.
The malware's latest version also features batter evasion, now specifically checking for the presence of Frida, a dynamic instrumentation toolkit popular among security analysts.
It also checks the device root status, searches for specific binaries associated with it, verifies if the system partition is mounted as read-only, and checks if development settings and ADB are enabled on the device.
The Mandrake threat remains alive, and while the five apps identified as droppers by Kaspersky are no longer available on Google Play, the malware could return via new, harder-to-detect apps.
Android users are recommended only to install apps from reputable publishers, check user comments before installing, avoid granting requests for risky permissions that seem unrelated to an app's function, and make sure that Play Protect is always active.
Google shared the following statement about the malicious apps found on Google Play.
"Google Play Protect is continuously improving with each app identified. We're always enhancing its capabilities, including upcoming live threat detection to help combat obfuscation and anti-evasion techniques," Google told BleepingComputer.
"Android users are automatically protected against known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play."









Comments
NoneRain - 3 months ago
App in PlayStore found bypassing Google Play Protect.
Play Protect: "Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play"
Makes sense.