
A new Android malware named FjordPhantom has been discovered using virtualization to run malicious code in a container and evade detection.
The malware was discovered by Promon, whose analysts report that it currently spreads via emails, SMS, and messaging apps targeting banking apps in Indonesia, Thailand, Vietnam, Singapore, and Malaysia.
Victims are tricked into downloading what appear to be legitimate banking apps but contain malicious code running in a virtual environment to attack the real banking app.
FjordPhantom aims to steal online bank account credentials and manipulate transactions by performing on-device fraud.
Promon's report highlights a case of FjordPhantom stealing $280,000 from a single victim, made possible by combining the malware's evasive nature with social engineering, such as calls supposedly from bank customer service agents.
Virtualization as evasion on Android
On Android, multiple apps can run in isolated environments known as "containers" for legitimate reasons, such as running multiple instances of the same app using different accounts.
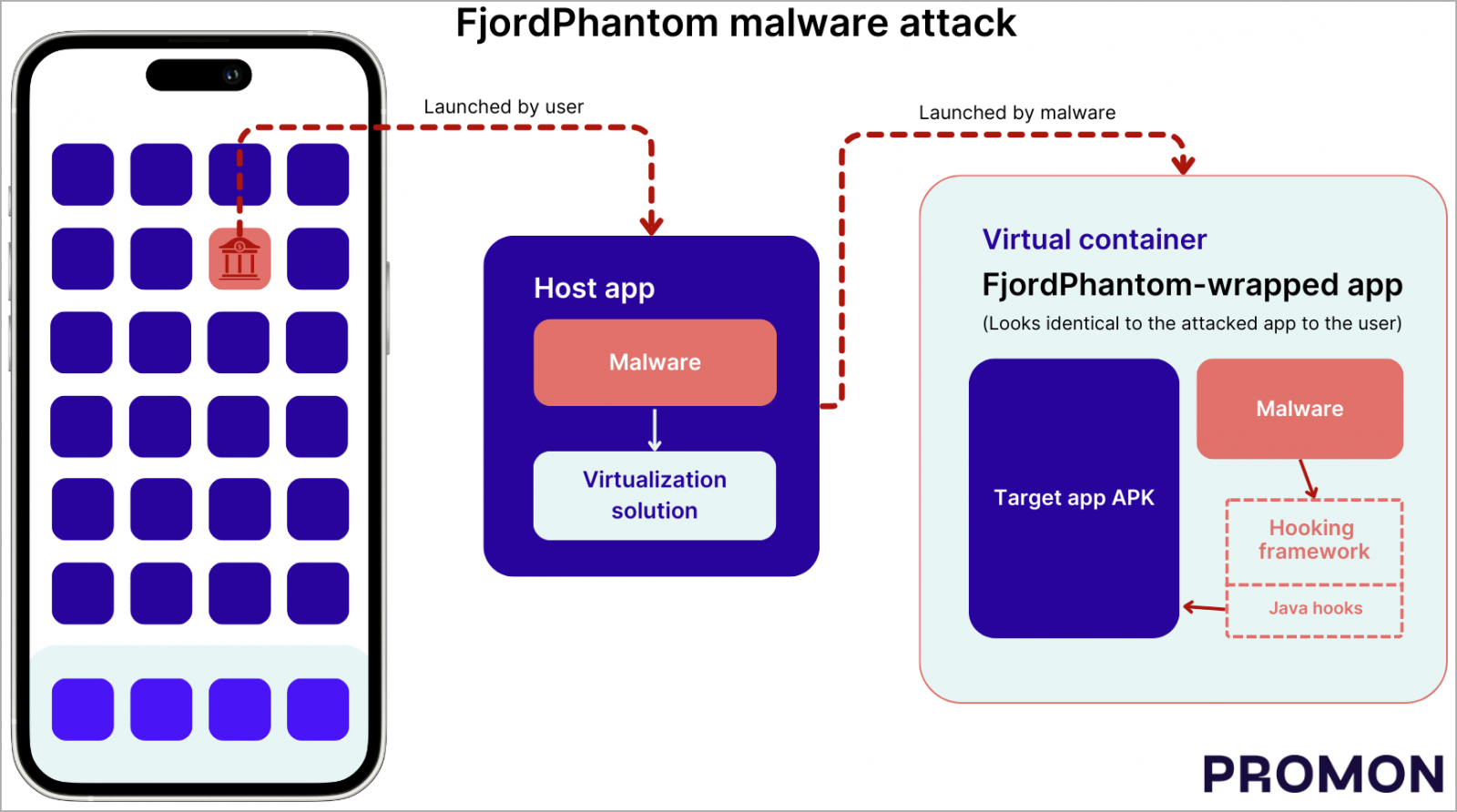
FjordPhantom incorporates a virtualization solution from open-source projects to create a virtual container on the device without the user knowing.
Upon launch, the malware installs the APK of the banking app the user intended to download and executes malicious code within the same container, making it part of the trusted process.
With the banking app running inside its virtual container, FjordPhantom can inject its code to hook key APIs that enable it to capture credentials, manipulate transactions, intercept sensitive information, etc.
In some apps, the malware's hooking framework also manipulates user interface elements to automatically close warning dialogs and keep the victim unaware of the compromise.
Source: Promon
Promon notes that this virtualization trick breaks the 'Android Sandbox' security concept, which prevents apps from accessing each other's data or interfering with their operations, as apps inside a container share the same sandbox.
This is a particularly sneaky attack because the banking app itself isn't modified, so code tampering detection doesn't help catch the threat.
Moreover, by hooking APIs related to GooglePlayServices, to make them appear unavailable on the device, FjordPhantom hampers root-related security checks.
The malware's hooks even extend to logging, potentially providing pointers to the developers on performing more targeted attacks on different apps.
Promon comments that this is a sign of active development, elevating the risk of FjordPhantom expanding its targeting scope beyond the mentioned countries in future releases.
Update 12/2 - A Google spokesperson has sent BleepingComputer the following comment regarding the FjordPhantom threat:
Users are protected by Google Play Protect, which can warn users or block apps known to exhibit malicious behavior on Android devices with Google Play Services, even when those apps come from sources outside of Google Play.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now