
Article updated to add information from CyberPanel developer and with information on free decryptor.
Over 22,000 CyberPanel instances exposed online to a critical remote code execution (RCE) vulnerability were mass-targeted in a PSAUX ransomware attack that took almost all instances offline.
This week, security researcher DreyAnd disclosed that CyberPanel 2.3.6 (and likely 2.3.7) suffers from three distinct security problems that can result in an exploit allowing unauthenticated remote root access without authentication.
Specifically, the researcher uncovered the following problems on CyberPanel version 2.3.6:
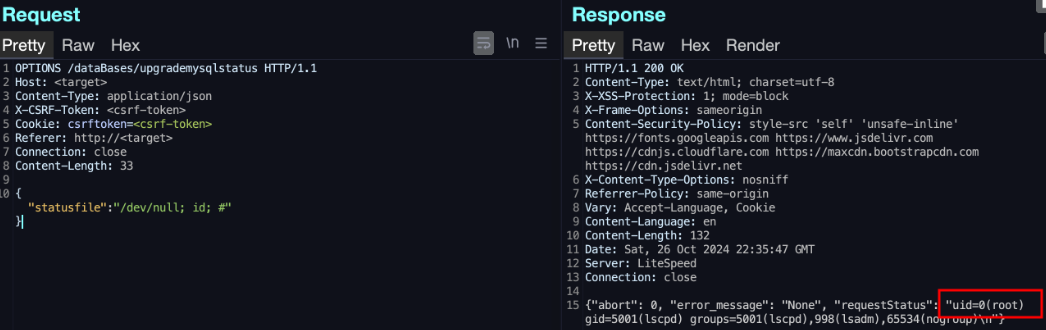
- Defective authentication: CyberPanel checks for user authentication (login) on each page separately instead of using a central system, leaving certain pages or routes, like ‘upgrademysqlstatus,’ unprotected from unauthorized access.
- Command injection: User inputs on unprotected pages aren’t properly sanitized, enabling attackers to inject and execute arbitrary system commands.
- Security filter bypass: The security middleware only filters POST requests, allowing attackers to bypass it using other HTTP methods, like OPTIONS or PUT.
Source: DreyAnd
The researcher, DreyAnd, developed a proof-of-concept exploit to demonstrate root-level remote command execution on the server, allowing him to take complete control of the server.
DreyAnd told BleepingComputer that he could only test the exploit on version 2.3.6 as he did not have access to the 2.3.7 version at the time. However, as 2.3.7 was released on September 19, before the bug was found, it was likely impacted as well.
The researcher said they disclosed the flaw to the CyberPanel developers on October 23, 2024, and a fix for the authentication issue was submitted later that evening on GitHub.
After publication of this story, CyberPanel creator Usman Nasir told BleepingComputer that version 2.3.8 was released and the bug fixed within thirty minutes of receiving the security disclosure.
Nasir says his team has been busy helping people with the upgrade and breaches, which is why they could not prepare the change log yet.
The developer told BleepingComputer that the recommended way to upgrade CyberPanel to the latest version can be found in this support article.
CyberPanel has also published a security advisory about the exploit and the ongoing attacks, with steps on how users should secure their systems.
Targeted in PSAUX ransomware attack
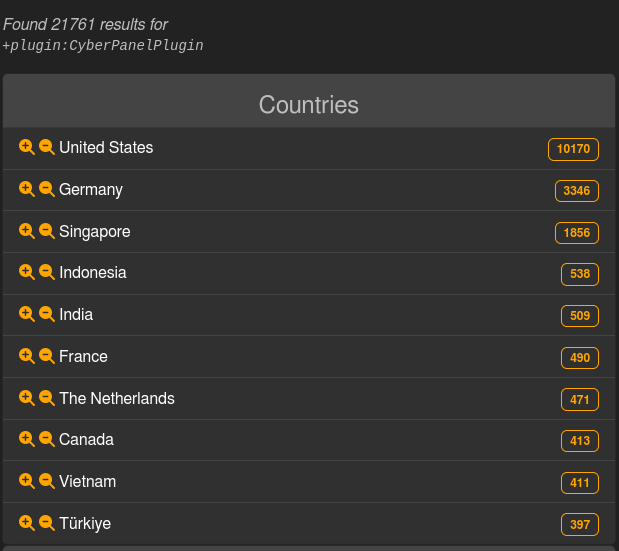
Yesterday, the threat intel search engine LeakIX reported that 21,761 vulnerable CyberPanel instances were exposed online, and nearly half (10,170) were in the United States.
Source: LeakIX | X
However, overnight, the number of instances mysteriously dropped to only about 400 instances, with LeakIX telling BleepingComputer the impacted servers are no longer accessible.
Cybersecurity researcher Gi7w0rm tweeted on X that these instances managed over 152,000 domains and databases, for which CyberPanel acted as the central access and management system.
LeakIX has now told BleepingComputer that threat actors mass-exploited the exposed CyberPanel servers to install the PSAUX ransomware.
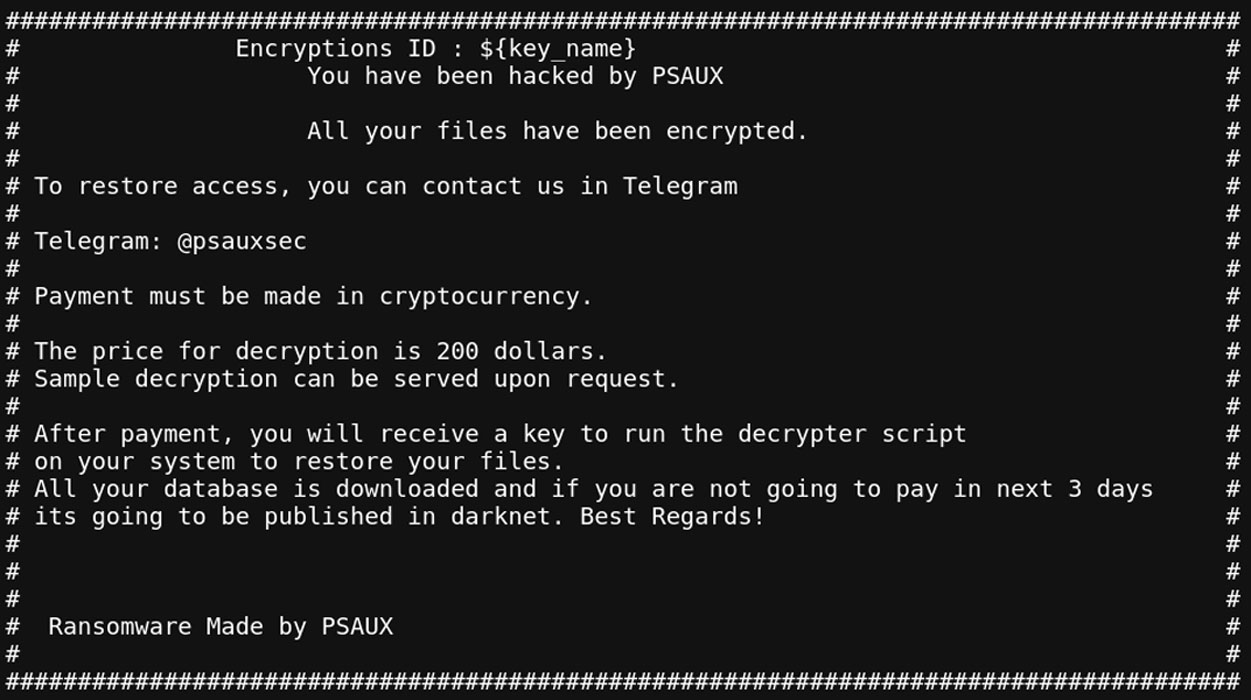
The PSAUX ransomware operation has been around since June 2024 and targets exposed web servers through vulnerabilities and misconfigurations.
Source: LeakIX
When launched on a server, the ransomware will create a unique AES key and IV and use them to encrypt the files on a server. Encrypted files will have the .psaux extension appended to the filename.
The ransomware will also create ransom notes named index.html in every folder and copy the ransom note to /etc/motd, so it is shown when a user logs into the device.
When finished, the AES key and IV are encrypted using an enclosed RSA key and saved as /var/key.enc and /var/iv.enc.
LeakIX and Chocapikk obtained the scripts used in this attack, which include an ak47.py script for exploiting the CyberPanel vulnerability and another script named actually.sh to encrypt the files.
Due to a flaw in how the PSAUX ransomware encrypted files, it is possible to decrypt files for free using a decryptor created by LeakIX.
It should be noted that if the threat actor utilized different encryption keys, then decrypting with the wrong one could corrupt your data. Therefore, be sure to make a backup of your data before attempting to use this decryptor to first test that it works.
After publication of our story, LeakIX determined the a cryptominer was installed along with the PSAUX ransomware and that two other ransomware operations targeted the flaw as well, with these variants appending either the .locked or .encrypted extensions to encrypted file's names.
Due to the active exploitation of the CyberPanel flaw, users are strongly advised to upgrade to the latest version on GitHub as soon as possible.
Update 10/29/24: Added information about decryptor.
Update 10/30/24: Integrated information from CyberPanel developer. Added security advisory from CyberPanel.
Update 10/30/24: Added information about other ransomware operations targeting the CyberPanel flaw and cryptominers.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now