Through a large malspam campaign, Locky is back and currently being heavily distributed worldwide. While Locky was at one point considered the largest distributed ransomware, over time it became much more common to see other ransomware such as Cerber, Spora, and now even GlobeImposter. While it is too soon to tell if this is just another brief surge or an attempt to become a large player again, what we do know is that this particular campaign is strong with a wide distribution.
Locky Diablo6 variant being distributed via Spam Emails
Today, security researcher Racco42 discovered a new Locky malspam campaign that was pushing a new Locky variant that appends the .diablo6 extension. This campaign is being distributed through spam emails that contain subject lines similar to E [date] (random_numer).docx. For example, E 2017-08-09 (698).docx. The message body simply states "Files attached. Thanks".
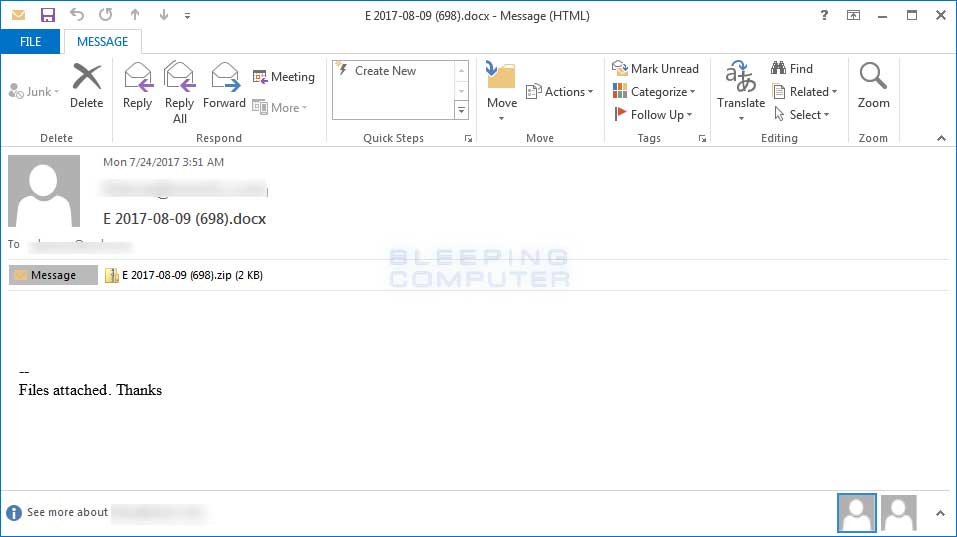
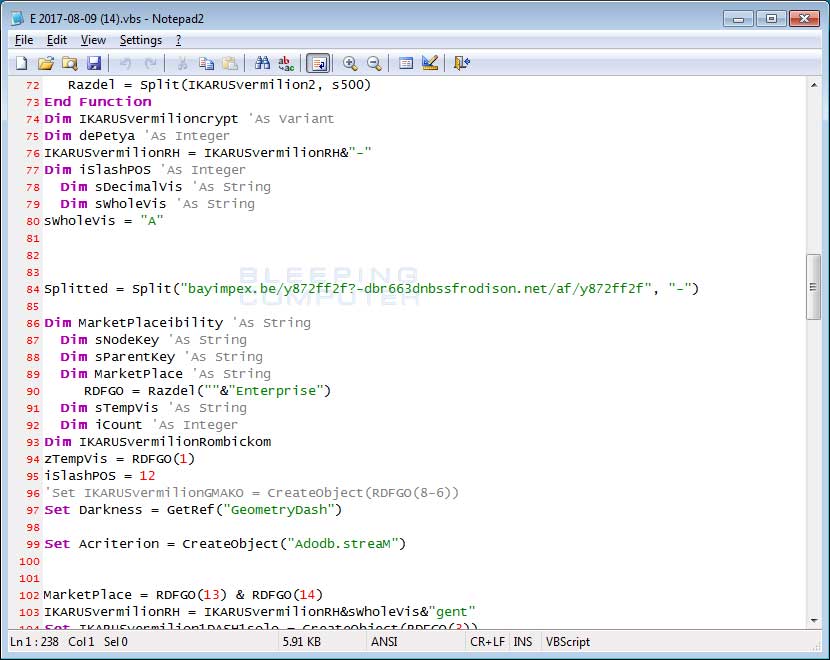
These emails have ZIP file attached that use the same name as the subject line, which contain a VBS downloader script. This script will contain one or more URLs that the script will use to download the Locky ransomware executable to the %Temp% folder and then execute it.
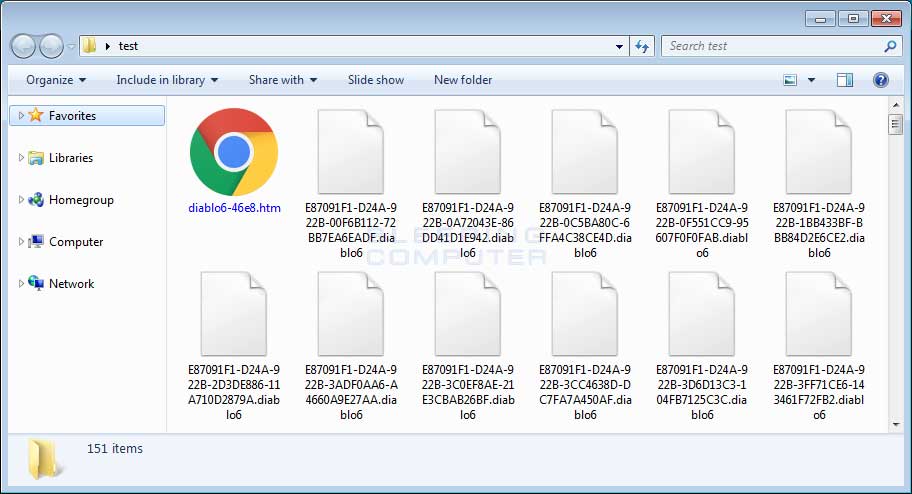
Once the file is downloaded and executed, it will scan the computer for files and encrypt them. When this Locky variant encrypts a file it will modify the file name and then append the .diablo6. When renaming the file, it uses the format [first_8_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[4_hexadecimal_chars]-[12_hexadecimal_chars].diablo6.
This means that a file named 1.png would be encrypted and named something like as E87091F1-D24A-922B-00F6B112-72BB7EA6EADF.diablo6.
When Locky has finished encrypting the computer, it will remove the downloaded executable and then display a ransom note that provides information on how to pay the ransom. The names of these ransom notes have changed for this version to diablo6-[random].htm.
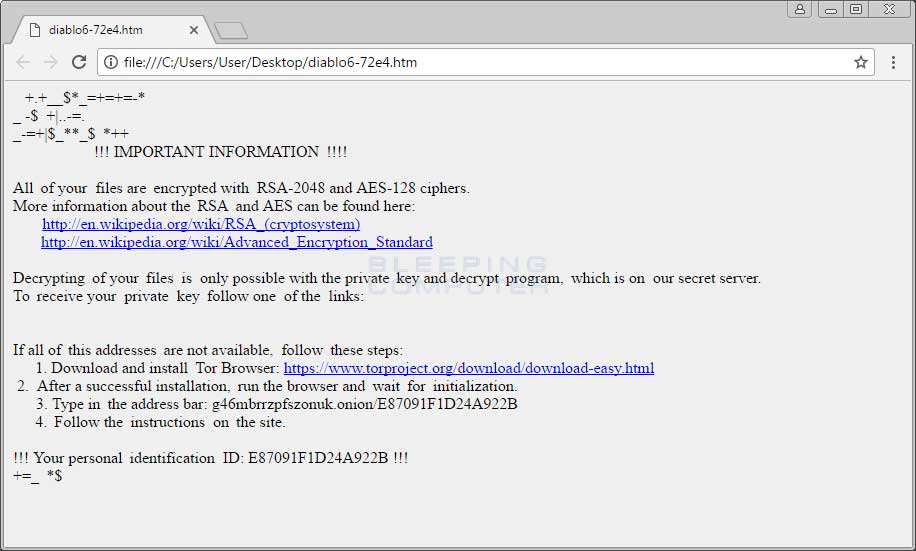
At the time of this writing, the Locky Decryptor TOR payment site has the ransom set to .49 BTC or approximately $1,600 USD.
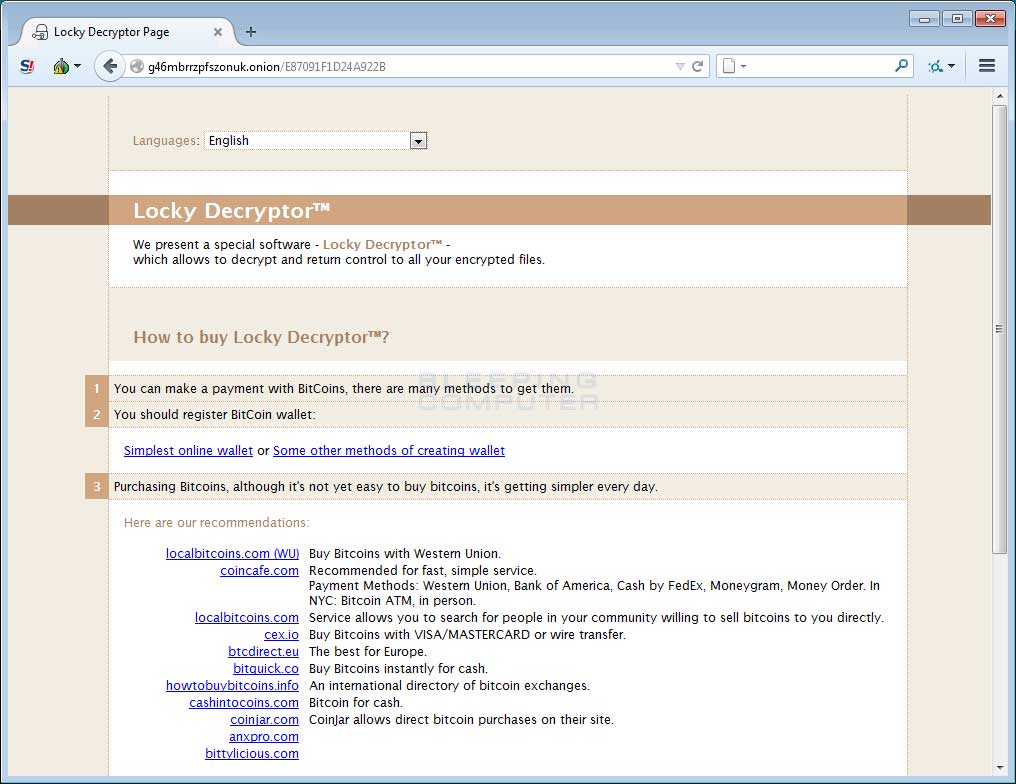
It is not possible to decrypt the Locky Ransomware Diablo6 Variant
Unfortunately, at this time it is still not possible to decrypt .diablo6 files encrypted by the Locky Ransomware for free.
The only way to recover encrypted files is via a backup, or if you are incredibly lucky, through Shadow Volume Copies. Though Locky does attempt to remove Shadow Volume Copies, in rare cases ransomware infections fail to do so for whatever reason. Due to this, if you do not have a viable backup, I always suggest people try as a last resort to restore encrypted files from Shadow Volume Copies as well.
For those who wish to discuss the Locky ransomware or need support, you can use our dedicated Locky Ransomware Help & Support Topic.









Comments
woody188 - 7 years ago
We started seeing these 8/9 too. We were lucky our AV was able to break the malware cycle at the VBS/Trojan stage so none of our customers were able to activate the script. Dodged another bullet!
G95 - 7 years ago
E 2017-08-09 (50).jpg VBS/Downldr.HM
E 2017-08-09 (50).jpg VBS/Vibrio.B
E 2017-08-09 (640).tiff VBS/Downldr.HM
E 2017-08-09 (640).tiff VBS/Vibrio.B