
Threat actors are abusing DocuSign's Envelopes API to create and mass-distribute fake invoices that appear genuine, impersonating well-known brands like Norton and PayPal.
Using a legitimate service, the attackers bypass email security protections as they come from an actual DocuSign domain, docusign.net.
The goal is to have their targets e-sign the documents, which they can then use to authorize payments independently from the company's billing departments.

Source: Wallarm
Sending realistic signature requests
DocuSign is an electronic signature platform that enables digitally signing, sending, and managing documents.
The Envelopes API is a core component of DocuSign's eSignature REST API, allowing developers to create, send, and manage document containers (envelopes) that define the signing process.
The API is meant to help customers automate the sending of documents that need signing, track their status, and retrieve them when signed.
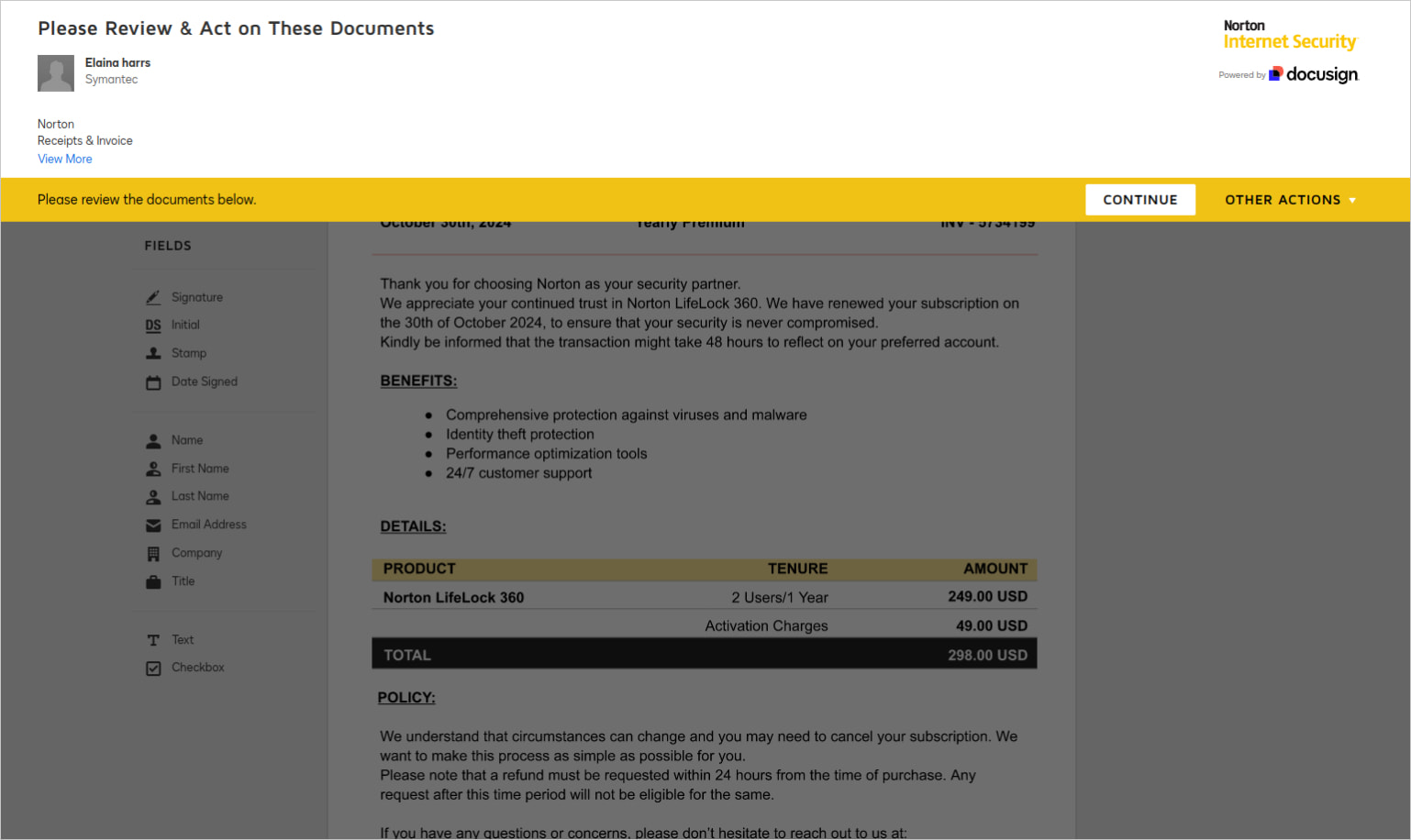
According to Wallarm security researchers, threat actors using legitimate paid DocuSign accounts ary abusing this API to send fake invoices that mimic the look and feel of reputable software firms.
Those users enjoy full access to the platform's templates, allowing them to design documents that resemble the impersonated entity's branding and layout.
Next, they use 'Envelopes: create' API function to generate and send a high volume of fraudulent invoices to many potential victims.
Source: Wallarm
Wallarm says the fees presented in these invoices are kept to a realistic range to increase the sense of legitimacy of the signing request.
"If users e-sign this document, the attacker can use the signed document to request payment from the organization outside of DocuSign or send the signed document through DocuSign to the finance department for payment," explains Wallarm.
"Other attempts have included different invoices with different items, usually following the same pattern of getting signatures for invoices that then authorize payment into the attackers bank accounts."
Large-scale DocuSign abuse
Wallarm notes that this type of abuse, which it has reported to DocuSign, has been going on for a while now, and customers have reported the campaigns many times on the platform's community forums.
"I'm suddenly getting 3-5 phishing emails a week from the docusign.net domain and none of the standard reporting email addresses like abuse@ or admin@ work," a customer posted to the DocuSign forums.
"They reject my email, and I can’t find any reporting information on their FAQ page. I guess I'm left with the choice of blocking the domain?"
The attacks appear automated rather than low-volume manual attempts, so the abuse occurs on a large scale that should be hard for the platform to miss.
BleepingComputer has contacted DocuSign to ask about their anti-abuse measures and if they plan to enhance them against the reported activity, but a comment wasn't immediately available.
Unfortunately, API endpoints are hard to secure when the threat actors create commercial accounts allowing access to these features.
Some recent examples of how hackers have abused APIs in the past include verifying the phone numbers of millions of Authy users, scraping the information of 49 million Dell customers, and linking email addresses to 15 million Trello accounts.
Update 11/5: DocuSign sent BleepingComputer the following comment:
We are aware of the reports and take them very seriously. While, in the interest of security, we don’t disclose specifics that could alert bad actors to our prevention tactics, Docusign has a number of technical systems and teams in place to help prevent misuse of our services.
We continuously monitor several layers of our systems to identify behaviors that are associated with fraud and illegal activity so we can quickly investigate and act to stop suspicious behavior. - DocuSign spokesperson
DocuSign provides more details about its proactive efforts and deterring techniques here.









Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now