
Today is Microsoft's September 2024 Patch Tuesday, which includes security updates for 79 flaws, including three actively exploited and one publicly disclosed zero-days.
This Patch Tuesday fixed seven critical vulnerabilities, which were either remote code execution or elevation of privileges flaws.
The number of bugs in each vulnerability category is listed below:
- 30 Elevation of Privilege Vulnerabilities
- 4 Security Feature Bypass Vulnerabilities
- 23 Remote Code Execution Vulnerabilities
- 11 Information Disclosure Vulnerabilities
- 8 Denial of Service Vulnerabilities
- 3 Spoofing Vulnerabilities
To learn more about the non-security updates released today, you can review our dedicated articles on the new Windows 11 KB5043076 cumulative update and Windows 10 KB5043064 update.
Four zero-days disclosed
This month's Patch Tuesday fixes three actively exploited, one of which was publicly disclosed, and another that reintroduces old CVEs so is marked as exploited.
Microsoft classifies a zero-day flaw as one that is publicly disclosed or actively exploited while no official fix is available.
The three actively exploited zero-day vulnerabilities in today's updates are:
CVE-2024-38014 - Windows Installer Elevation of Privilege Vulnerability
This vulnerability allows attacks to gain SYSTEM privileges on Windows systems.
Microsoft has not shared any details on how it was exploited in attacks.
The flaw was discovered by Michael Baer with SEC Consult Vulnerability Lab.
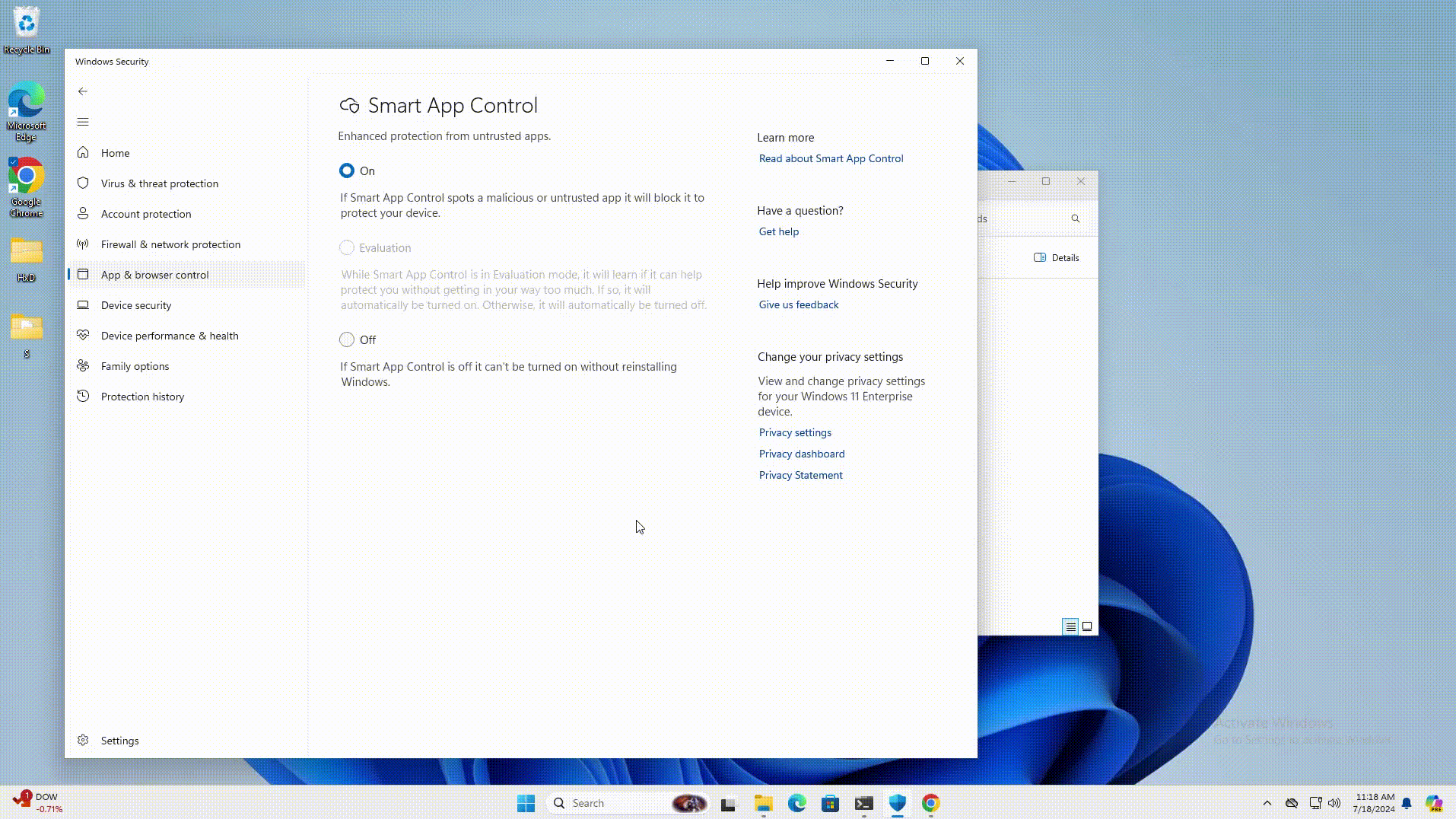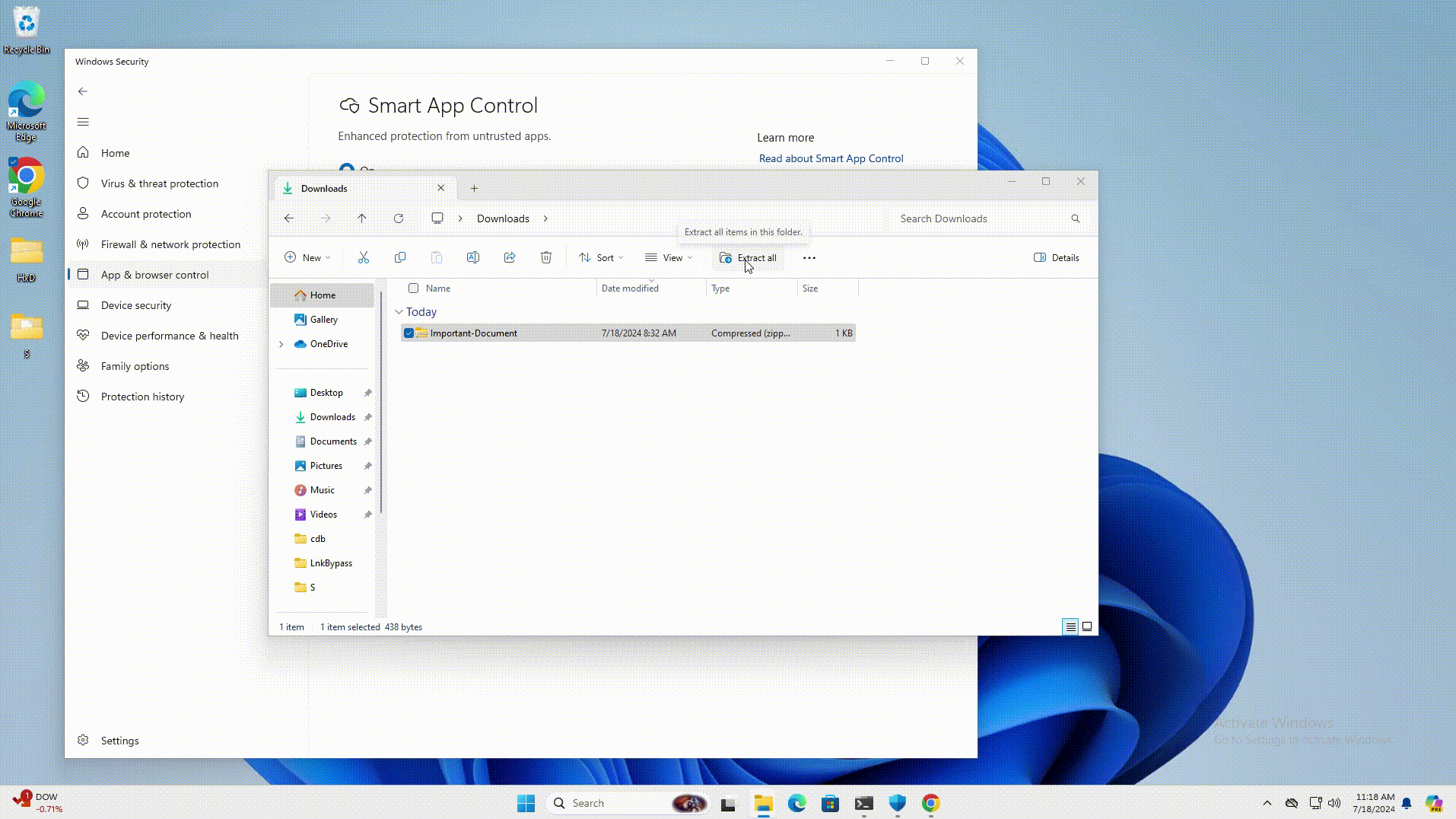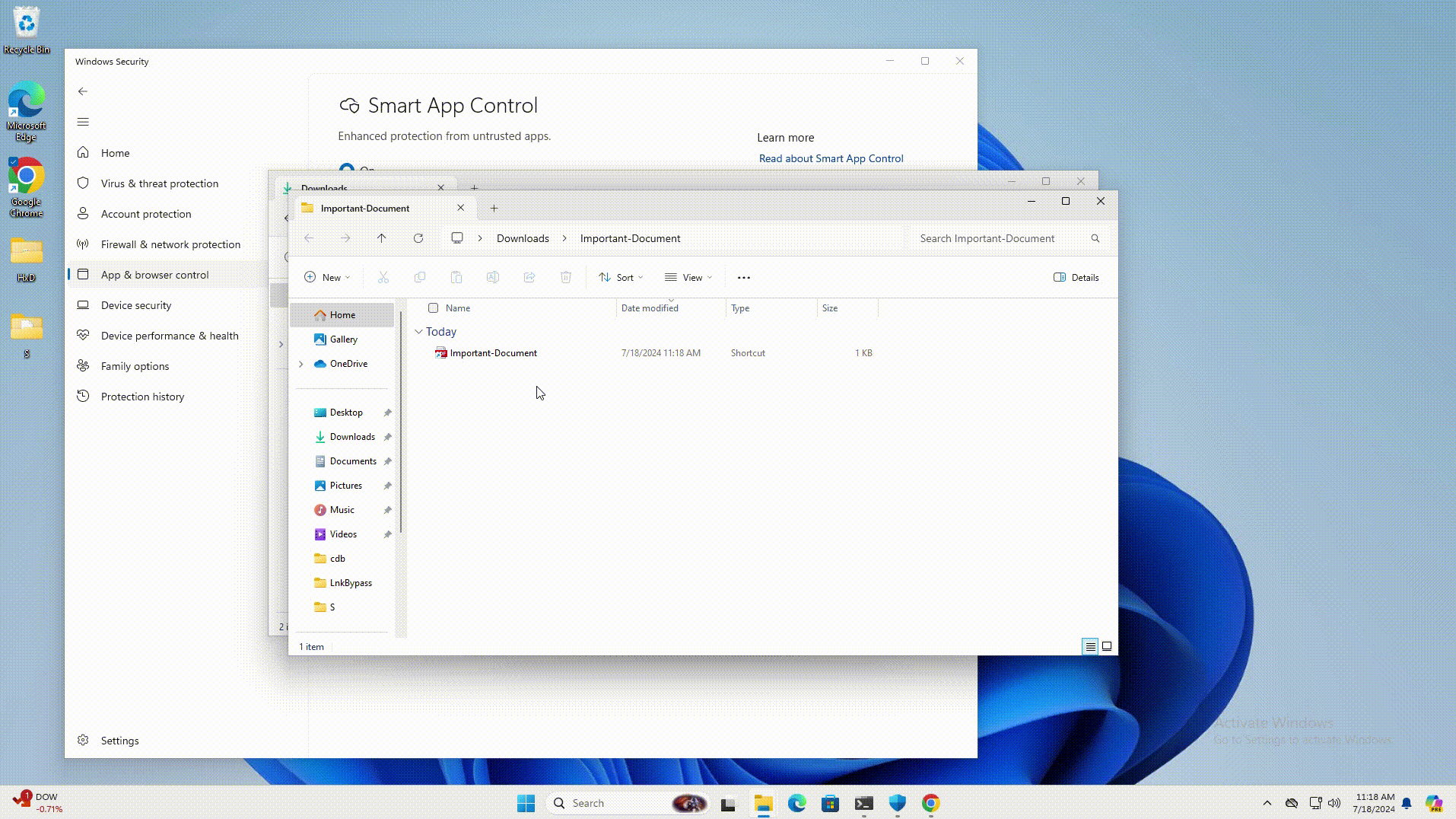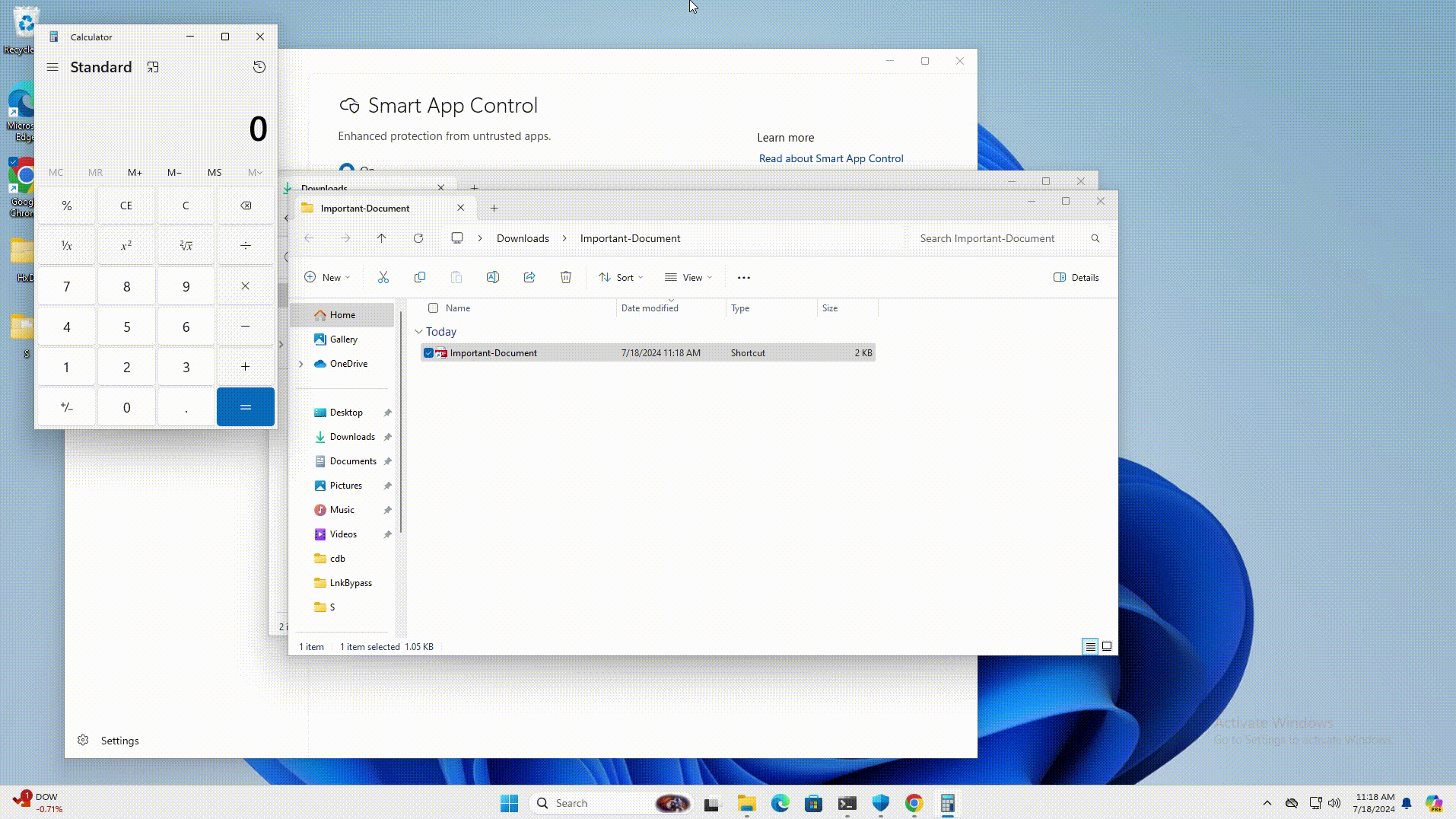
CVE-2024-38217 - Windows Mark of the Web Security Feature Bypass Vulnerability
This flaw was publicly disclosed last month by Joe Desimone of Elastic Security and is believed to have been actively exploited since 2018.
In the report, Desimone outlined a technique called LNK stomping that allows specially crafted LNK files with non-standard target paths or internal structures to cause the file to be opened while bypassing Smart App Control and the Mark of the Web security warnings.
"An attacker can craft a malicious file that would evade Mark of the Web (MOTW) defenses, resulting in a limited loss of integrity and availability of security features such as SmartScreen Application Reputation security check and/or the legacy Windows Attachment Services security prompt," explains Microsoft's advisory.
When exploited, it causes the command in the LNK file to be executed without a warning, as demonstrated in this video.
CVE-2024-38226 - Microsoft Publisher Security Feature Bypass Vulnerability
Microsoft fixed a Microsoft Publisher flaw that bypasses the security protections against embedded macros in downloaded documents.
"An attacker who successfully exploited this vulnerability could bypass Office macro policies used to block untrusted or malicious files," explains Microsoft's advisory.
Microsoft has not shared who disclosed the flaw and how it was exploited.
Microsoft also fixed a zero-day that is marked as exploited, but was done so as it can reintroduce older exploited flaws, as explained below.
CVE-2024-43491 - Microsoft Windows Update Remote Code Execution Vulnerability
Microsoft fixed a servicing stack flaw that is marked as remote code execution, but actually reintroduces a variety of vulnerabilities to previously patched programs.
"Microsoft is aware of a vulnerability in Servicing Stack that has rolled back the fixes for some vulnerabilities affecting Optional Components on Windows 10, version 1507 (initial version released July 2015)," explains Microsoft's advisory.
"This means that an attacker could exploit these previously mitigated vulnerabilities on Windows 10, version 1507 (Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 LTSB) systems that have installed the Windows security update released on March 12, 2024—KB5035858 (OS Build 10240.20526) or other updates released until August 2024. All later versions of Windows 10 are not impacted by this vulnerability."
"This servicing stack vulnerability is addressed by installing the September 2024 Servicing stack update (SSU KB5043936) AND the September 2024 Windows security update (KB5043083), in that order."
This flaw only impacts Windows 10, version 1507, which reached the end of life in 2017. However, it also impacts Windows 10 Enterprise 2015 LTSB and Windows 10 IoT Enterprise 2015 LTSB editions, which are still under support.
This flaw is interesting because it caused Optional Components, such as Active Directory Lightweight Directory Services, XPS Viewer, Internet Explorer 11, LPD Print Service, IIS, and Windows Media Player to roll back to their original RTM versions.
This caused any previous CVE to be reintroduced into the program, which could then be exploited.
Microsoft marked this flaw as exploited because its reintroduced vulnerabilities that have been actively exploited in the past. However, Microsoft says the flaw itself was discovered internally by Microsoft and it has seen no evidence that it is publicly known by others.
More details about the flaw and the complete list of affected components can found in Microsoft's advisory.
Recent updates from other companies
Other vendors who released updates or advisories in September 2024 include:
- Apache fixes a critical OFBiz remote code execution vulnerability that was a bypass for previously fixed flaws.
- Cisco fixed multiple vulnerabilities this month, including a backdoor admin account in Smart Licensing Utility and a command injection vulnerability in ISE.
- Eucleak attack extracts ECDSA secret keys to clone YubiKey FIDO devices.
- Fortinet released security updates for flaws in Fortisandbox and FortiAnalyzer & FortiManager.
- Google backported a fix for an actively exploited Pixel elevation of privileges flaw to other Android devices.
- Ivanti releases security updates for critical vTM auth bypass with public exploit.
- LiteSpeed Cache plugin for Wordpress fixes an unauthenticated account takeover issue.
- A SonicWall access control flaw fixed last month is now exploited in ransomware attacks.
- Veeam fixes a critical RCE vulnerability in Backup & Replication software
- Zyxel warned of a critical OS command injection flaw in its routers.
The September 2024 Patch Tuesday Security Updates
Below is the complete list of resolved vulnerabilities in the September 2024 Patch Tuesday updates.
To access the full description of each vulnerability and the systems it affects, you can view the full report here.
| Tag | CVE ID | CVE Title | Severity |
|---|---|---|---|
| Azure CycleCloud | CVE-2024-43469 | Azure CycleCloud Remote Code Execution Vulnerability | Important |
| Azure Network Watcher | CVE-2024-38188 | Azure Network Watcher VM Agent Elevation of Privilege Vulnerability | Important |
| Azure Network Watcher | CVE-2024-43470 | Azure Network Watcher VM Agent Elevation of Privilege Vulnerability | Important |
| Azure Stack | CVE-2024-38216 | Azure Stack Hub Elevation of Privilege Vulnerability | Critical |
| Azure Stack | CVE-2024-38220 | Azure Stack Hub Elevation of Privilege Vulnerability | Critical |
| Azure Web Apps | CVE-2024-38194 | Azure Web Apps Elevation of Privilege Vulnerability | Critical |
| Dynamics Business Central | CVE-2024-38225 | Microsoft Dynamics 365 Business Central Elevation of Privilege Vulnerability | Important |
| Microsoft AutoUpdate (MAU) | CVE-2024-43492 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability | Important |
| Microsoft Dynamics 365 (on-premises) | CVE-2024-43476 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability | Important |
| Microsoft Graphics Component | CVE-2024-38247 | Windows Graphics Component Elevation of Privilege Vulnerability | Important |
| Microsoft Graphics Component | CVE-2024-38250 | Windows Graphics Component Elevation of Privilege Vulnerability | Important |
| Microsoft Graphics Component | CVE-2024-38249 | Windows Graphics Component Elevation of Privilege Vulnerability | Important |
| Microsoft Management Console | CVE-2024-38259 | Microsoft Management Console Remote Code Execution Vulnerability | Important |
| Microsoft Office Excel | CVE-2024-43465 | Microsoft Excel Elevation of Privilege Vulnerability | Important |
| Microsoft Office Publisher | CVE-2024-38226 | Microsoft Publisher Security Feature Bypass Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2024-38227 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2024-43464 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Critical |
| Microsoft Office SharePoint | CVE-2024-38018 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Critical |
| Microsoft Office SharePoint | CVE-2024-38228 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Important |
| Microsoft Office SharePoint | CVE-2024-43466 | Microsoft SharePoint Server Denial of Service Vulnerability | Important |
| Microsoft Office Visio | CVE-2024-43463 | Microsoft Office Visio Remote Code Execution Vulnerability | Important |
| Microsoft Outlook for iOS | CVE-2024-43482 | Microsoft Outlook for iOS Information Disclosure Vulnerability | Important |
| Microsoft Streaming Service | CVE-2024-38245 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability | Important |
| Microsoft Streaming Service | CVE-2024-38241 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability | Important |
| Microsoft Streaming Service | CVE-2024-38242 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability | Important |
| Microsoft Streaming Service | CVE-2024-38244 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability | Important |
| Microsoft Streaming Service | CVE-2024-38243 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability | Important |
| Microsoft Streaming Service | CVE-2024-38237 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability | Important |
| Microsoft Streaming Service | CVE-2024-38238 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability | Important |
| Power Automate | CVE-2024-43479 | Microsoft Power Automate Desktop Remote Code Execution Vulnerability | Important |
| Role: Windows Hyper-V | CVE-2024-38235 | Windows Hyper-V Denial of Service Vulnerability | Important |
| SQL Server | CVE-2024-37338 | Microsoft SQL Server Native Scoring Remote Code Execution Vulnerability | Important |
| SQL Server | CVE-2024-37980 | Microsoft SQL Server Elevation of Privilege Vulnerability | Important |
| SQL Server | CVE-2024-26191 | Microsoft SQL Server Native Scoring Remote Code Execution Vulnerability | Important |
| SQL Server | CVE-2024-37339 | Microsoft SQL Server Native Scoring Remote Code Execution Vulnerability | Important |
| SQL Server | CVE-2024-37337 | Microsoft SQL Server Native Scoring Information Disclosure Vulnerability | Important |
| SQL Server | CVE-2024-26186 | Microsoft SQL Server Native Scoring Remote Code Execution Vulnerability | Important |
| SQL Server | CVE-2024-37342 | Microsoft SQL Server Native Scoring Information Disclosure Vulnerability | Important |
| SQL Server | CVE-2024-43474 | Microsoft SQL Server Information Disclosure Vulnerability | Important |
| SQL Server | CVE-2024-37335 | Microsoft SQL Server Native Scoring Remote Code Execution Vulnerability | Important |
| SQL Server | CVE-2024-37966 | Microsoft SQL Server Native Scoring Information Disclosure Vulnerability | Important |
| SQL Server | CVE-2024-37340 | Microsoft SQL Server Native Scoring Remote Code Execution Vulnerability | Important |
| SQL Server | CVE-2024-37965 | Microsoft SQL Server Elevation of Privilege Vulnerability | Important |
| SQL Server | CVE-2024-37341 | Microsoft SQL Server Elevation of Privilege Vulnerability | Important |
| Windows Admin Center | CVE-2024-43475 | Microsoft Windows Admin Center Information Disclosure Vulnerability | Important |
| Windows AllJoyn API | CVE-2024-38257 | Microsoft AllJoyn API Information Disclosure Vulnerability | Important |
| Windows Authentication Methods | CVE-2024-38254 | Windows Authentication Information Disclosure Vulnerability | Important |
| Windows DHCP Server | CVE-2024-38236 | DHCP Server Service Denial of Service Vulnerability | Important |
| Windows Installer | CVE-2024-38014 | Windows Installer Elevation of Privilege Vulnerability | Important |
| Windows Kerberos | CVE-2024-38239 | Windows Kerberos Elevation of Privilege Vulnerability | Important |
| Windows Kernel-Mode Drivers | CVE-2024-38256 | Windows Kernel-Mode Driver Information Disclosure Vulnerability | Important |
| Windows Libarchive | CVE-2024-43495 | Windows libarchive Remote Code Execution Vulnerability | Important |
| Windows Mark of the Web (MOTW) | CVE-2024-38217 | Windows Mark of the Web Security Feature Bypass Vulnerability | Important |
| Windows Mark of the Web (MOTW) | CVE-2024-43487 | Windows Mark of the Web Security Feature Bypass Vulnerability | Moderate |
| Windows MSHTML Platform | CVE-2024-43461 | Windows MSHTML Platform Spoofing Vulnerability | Important |
| Windows Network Address Translation (NAT) | CVE-2024-38119 | Windows Network Address Translation (NAT) Remote Code Execution Vulnerability | Critical |
| Windows Network Virtualization | CVE-2024-38232 | Windows Networking Denial of Service Vulnerability | Important |
| Windows Network Virtualization | CVE-2024-38233 | Windows Networking Denial of Service Vulnerability | Important |
| Windows Network Virtualization | CVE-2024-38234 | Windows Networking Denial of Service Vulnerability | Important |
| Windows Network Virtualization | CVE-2024-43458 | Windows Networking Information Disclosure Vulnerability | Important |
| Windows PowerShell | CVE-2024-38046 | PowerShell Elevation of Privilege Vulnerability | Important |
| Windows Remote Access Connection Manager | CVE-2024-38240 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | Important |
| Windows Remote Desktop Licensing Service | CVE-2024-38231 | Windows Remote Desktop Licensing Service Denial of Service Vulnerability | Important |
| Windows Remote Desktop Licensing Service | CVE-2024-38258 | Windows Remote Desktop Licensing Service Information Disclosure Vulnerability | Important |
| Windows Remote Desktop Licensing Service | CVE-2024-43467 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | Important |
| Windows Remote Desktop Licensing Service | CVE-2024-43454 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | Important |
| Windows Remote Desktop Licensing Service | CVE-2024-38263 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | Important |
| Windows Remote Desktop Licensing Service | CVE-2024-38260 | Windows Remote Desktop Licensing Service Remote Code Execution Vulnerability | Important |
| Windows Remote Desktop Licensing Service | CVE-2024-43455 | Windows Remote Desktop Licensing Service Spoofing Vulnerability | Important |
| Windows Security Zone Mapping | CVE-2024-30073 | Windows Security Zone Mapping Security Feature Bypass Vulnerability | Important |
| Windows Setup and Deployment | CVE-2024-43457 | Windows Setup and Deployment Elevation of Privilege Vulnerability | Important |
| Windows Standards-Based Storage Management Service | CVE-2024-38230 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability | Important |
| Windows Storage | CVE-2024-38248 | Windows Storage Elevation of Privilege Vulnerability | Important |
| Windows TCP/IP | CVE-2024-21416 | Windows TCP/IP Remote Code Execution Vulnerability | Important |
| Windows TCP/IP | CVE-2024-38045 | Windows TCP/IP Remote Code Execution Vulnerability | Important |
| Windows Update | CVE-2024-43491 | Microsoft Windows Update Remote Code Execution Vulnerability | Critical |
| Windows Win32K - GRFX | CVE-2024-38246 | Win32k Elevation of Privilege Vulnerability | Important |
| Windows Win32K - ICOMP | CVE-2024-38252 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability | Important |
| Windows Win32K - ICOMP | CVE-2024-38253 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability | Important |
Update 9/11/24: Updated to explain that only three flaws were actively exploited and why CVE-2024-43491 was marked as exploited.









Comments
terapcpros - 2 months ago
after updates today the computer will no longer boot. all you get is a black screen. if you unplug for 5 minutes, the computer will then boot and then the screen goes black again after a few minutes. the only way to get it back on is to unplug for another 5 minutes. any help would be greatly apprecitaed.. thanks
NoneRain - 2 months ago
It does pass the boot screen, right? if so, boot up on a USB drive with Windows, and uninstall the last update.
https://www.winhelponline.com/blog/uninstall-windows-10-update-offline-windows-recovery/