
A vulnerability in the free version of Bitdefender Antivirus could be exploited by an attacker to get SYSTEM-level permissions, reserved for the most privileged account on a Windows machine.
Privilege escalation vulnerabilities are used in a later stage of an attack, after the threat actor already compromised the target host and needs elevated permissions to establish persistence or execute code with the privileges of the most powerful user.
Looking for missing DLL
Identified as CVE-2019-15295, the vulnerability is owed to lack of verification that loaded binaries are signed and come from a trusted location.
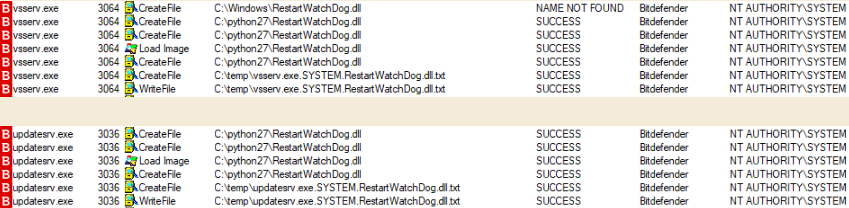
Peleg Hadar of SafeBreach Labs says that Bitdefender's security service (vsserv.exe) and the updater service (updatesrv.exe) started as signed processes with SYSTEM authority.
However, they tried to load a missing DLL file ('RestartWatchDog.dll') from various locations in the PATH environment variable.
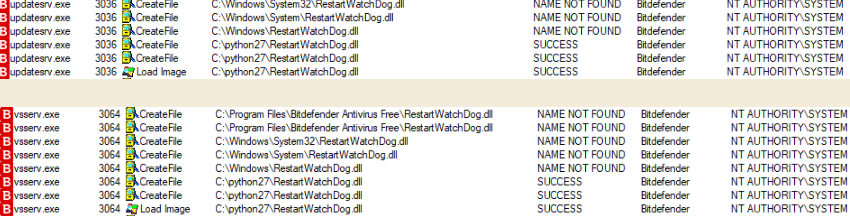
One of the locations is 'c:/python27,' which comes with an access control list (ACL) open to any authenticated user. This makes privilege escalation trivial because a user to normal permissions could write the missing DLL and have it loaded by Bitdefender's signed processes.
Hadar tested the theory with an unsigned DLL that wrote to a text file the name of the process loading it, the name of the user executing it, and the name of the DLL file.
His assumption was confirmed, and his 'RestartWatchDog.dll' file was loaded without a hitch.
The root of the issue is the ServiceInstance.dll library that attempts to load the missing DLL.
SafeBreach disclosed the vulnerability responsibly to Bitdefender on July 17 and on August 14 received validation from the antivirus maker.
On Monday, Bitdefender rolled out a patch for its Antivirus Free 2020 product. Users with an internet connection received the update automatically.
"An Untrusted Search Path vulnerability in the ServiceInstance.dll library versions 1.0.15.119 and lower, as used in Bitdefender Antivirus Free 2020 versions prior to 1.0.15.138, allows an attacker to load an arbitrary DLL file from the search path." reads Bitdefender's advisory
SafeBreach published last week a report on a similar DLL hijacking issue in Trend Micro's Password Manager.









Comments
DDE_server - 5 years ago
ooh good Article and breaking news