FireEye Blog: Your Locker of Information for CryptoLocker Decryption
The FireEye & Fox-IT decryptcryptolocker.com website posted this comment shortly before closing.FireEye is no longer providing decryption solutions for CryptoLocker. If your computer has recently been infected with ransomware, chances are that the infection has been caused by one of the many copycat attacks that use the same or similar name and method of operation. Since these new ransomware variants use different encryption keys, we have discontinued the DecryptCryptoLocker website and its associated decryption service.
In August 2014, we launched our website to help the victims of the CryptoLocker malware. We are happy to have helped more than five thousand individuals and small businesses. CryptoLocker, unfortunately, has inspired criminals all over the world. We have seen more than 20 copycat ransomware attacks since the original CryptoLocker, some of which use the same name, modus operandi and layout as the original CryptoLocker. We believe that our Decryptolocker site has served its purpose, and we have decommissioned it given that the threat landscape has evolved.
This topic was created in 2014 for help with the original CryptoLocker Ransomware which first appeared in the beginning of September 2013. The topic keeps being resurrected by folks incorrectly assuming their infection is the result of CryptoLocker ransomware when that is not the case.
CryptoLocker Ransomware does not exist anymore and hasn't since June 2014. There are many copycat ransomware variants which pretend to be or use the CryptoLocker name but those infections are not the same. Any references to CryptoLocker and retrieving keys for it will not work anymore.
If you need assistance with a ransomware infection, please read and follow the instructions in these topics.
- How to Post a Topic Asking for Help With Ransomware
- ID Ransomware for assistance with identification and confirmation
Thanks for you cooperation
The BC Staff
.
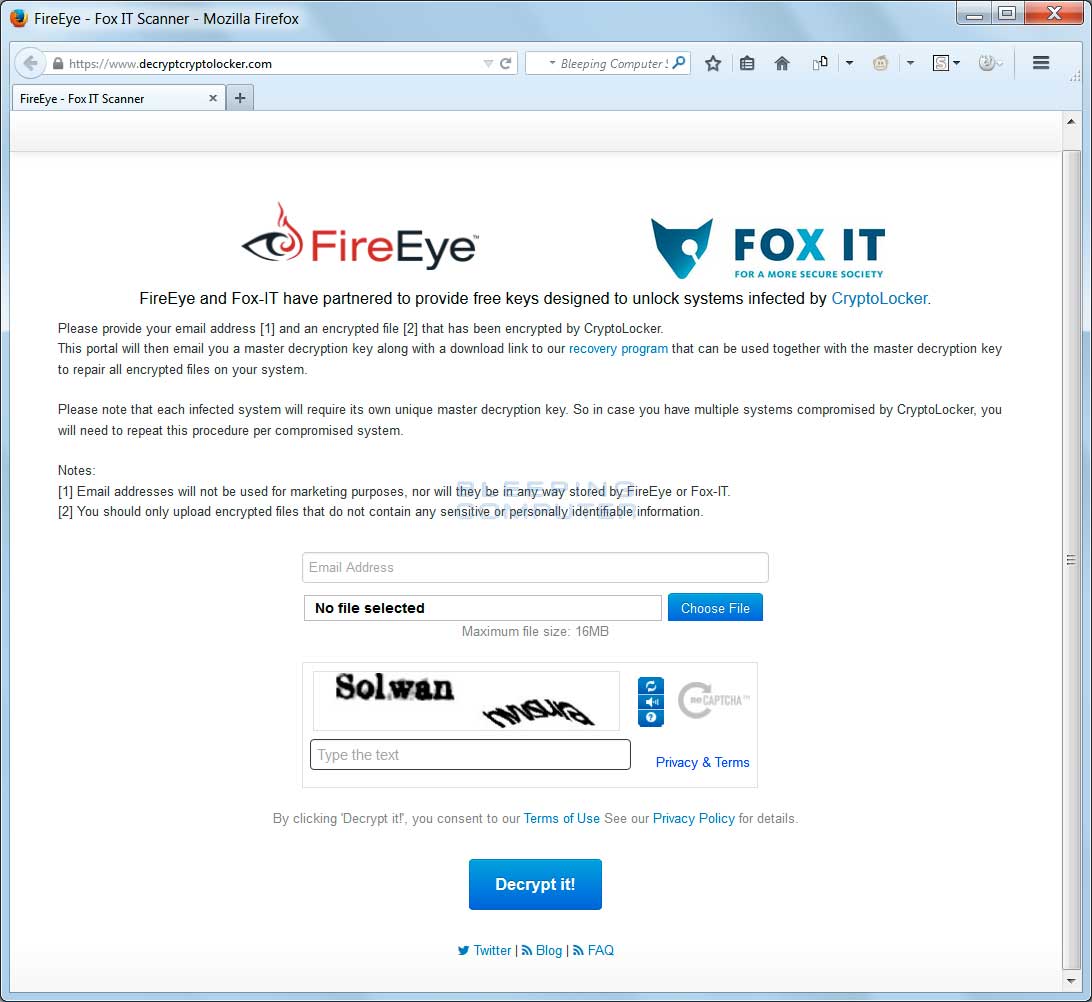
FireEye in collaboration with Fox-IT have released a way to possibly retrieve the private decryption key for those who were infected by the CryptoLocker infection. As covered extensively in the past, CryptoLocker was a ransomware program that encrypted the data files on an infected computer. In the past, the only way to decrypt your files was to pay the ransom in order to get a decryption key and decrypter. Recently, some of the servers associated with CryptoLocker and the Gameover malware distribution network were taken over by security firms and government agencies, which included FireEye and Fox-IT, during Operation Tovar. During this operation it appears that some of the decryption keys were discovered and are being made available.
In order to see if your decryption key is available, you need to go the site https://www.decryptcryptolocker.com. At this site you can upload one of your CryptoLocker encrypted files and an email address that you wish the key to be sent to. This service will then attempt to decrypt your file using all of the known private decryption keys, and if there is a match, will email you the key and instructions on how to decrypt the rest of your files.




 Back to top
Back to top